
ABOUT UAT
University of Advancing Technology is an elite, private college that serves its student body by fostering knowledge creation and academic excellence in an environment that embraces the young technophiles of the world. With three centers of research and a suite of technology-centered undergraduate and graduate degrees, the University is a recognized leader in technology education.

Technology Forensics plays a critical role in modern investigations as digital systems become central to business operations, communication, and security. From cybercrime and data breaches to corporate investigations and legal proceedings, organizations rely on digital evidence to uncover facts and protect assets. Earning a Technology Forensics degree equips students with the analytical and technical skills needed to investigate, preserve, and interpret digital data in real-world scenarios.
University of Advancing Technology (UAT) offers a career-focused Technology Forensics degree designed for students interested in cybersecurity, investigation, and digital evidence analysis. Located in Tempe, Arizona, UAT places students near the growing Phoenix technology and cybersecurity ecosystem, providing access to industry opportunities and applied learning experiences.
A Technology Forensics degree focuses on the identification, collection, analysis, and preservation of digital evidence across a variety of platforms and systems. Students develop both technical expertise and investigative problem-solving skills.
At UAT, students gain knowledge in areas such as:
Key Courses included to earn a degree in Technology Forensics
UAT’s project-based learning approach ensures students graduate with hands-on experience and practical investigative skills.
As cyber threats and digital crimes continue to increase, technology forensics professionals are in high demand across public and private sectors. Organizations depend on trained investigators to respond to incidents, support legal proceedings, and strengthen security practices.
A Technology Forensics degree prepares students to contribute to fields including:
These adaptable skills help graduates remain competitive as digital technologies, cyber threats, and regulatory requirements continue to evolve.
Graduates of UAT’s Technology Forensics degree program are prepared for careers that combine technology, investigation, and critical thinking.
Common career paths include:
As digital evidence becomes increasingly important, demand for technology forensics professionals continues to grow.
What careers can you pursue with a Technology Forensics degree?
Graduates can work in digital forensics, cybersecurity investigations, incident response, legal and corporate investigations, and compliance-related roles.
Is a Technology Forensics degree worth it?
Yes. Digital investigation and forensic skills are in demand across law enforcement, corporate security, legal, and cybersecurity sectors.
Where is the University of Advancing Technology located?
UAT is located in Tempe, Arizona, within the greater Phoenix technology corridor.
Does UAT offer hands-on Technology Forensics experience?
Yes. UAT emphasizes applied, project-based learning so students gain real-world investigative experience.
Do students need prior cybersecurity or forensic experience to enroll?
No. The program is designed to teach foundational concepts and progressively build advanced forensic and investigative skills.
How does UAT prepare students for technology forensics careers?
UAT focuses on real-world projects, industry-aligned tools, portfolio development, and interdisciplinary collaboration.
Turn your interest in cybersecurity and investigation into a career with the Technology Forensics degree at the University of Advancing Technology. Learn through hands-on projects, analyze real-world digital evidence, and build in-demand skills in Tempe, Arizona, near the heart of the Phoenix tech ecosystem.
Explore the Technology Forensics degree and start your future at UAT today. Learn More Now!

With the world more interconnected than ever, threats to personal and organizational data have grown in number and complexity. The digital world needs skilled defenders who can safeguard online interactions for individuals, businesses, and governments alike. Network security is the foundation of this protection, providing the tools and strategies to detect attacks, defend systems, and ensure safe digital operations. At University of Advancing Technology (UAT), the Network Security degree equips students with hands-on experience in cyber defense, encryption, penetration testing, and incident response—skills that prepare graduates to thrive in one of today’s fastest-growing career fields.
UAT’s Network Security degree focuses on proactive cyber defense strategies that blend theory with hands-on practice. Students gain experience in encryption, penetration testing, vulnerability assessment, and incident response while building a foundation around the core principles of confidentiality, integrity, and availability.
Graduates of the program will be able to:
Design secure network infrastructures with defense-in-depth strategies.
Install and configure security tools like firewalls, intrusion detection systems, and anti-malware software.
Automate security processes using scripts and system administration tools.
Develop and implement response and recovery plans for incidents, disasters, and business continuity.
Apply legal and ethical best practices in cybersecurity and information governance.
Research, evaluate, and mitigate emerging cyber threats across evolving digital landscapes.
This combination of technical training and practical application ensures UAT graduates are prepared to defend against today’s cyber threats while anticipating the challenges of tomorrow.
UAT stands out as a National Center of Academic Excellence in Cyber Defense (CAE-CD), a designation from the NSA that highlights the program’s quality and rigor. Students benefit from UAT’s Synchronic Learning model, which blends mentorship, hands-on labs, and project-based education. Along the way, they tackle real-world challenges through cyber competitions and proof-of-concept innovations that prepare them for the workforce.
Here are some of the key courses that bring the program to life:
NTW220: Linux I for Technologists – gaining command-line and open-source system experience.
NTW245: Mobile Security and Exploitation– securing modern mobile and cloud environments.
NTW280: Virtualization System Technologies and Administration – exploring virtualization for secure, scalable networks.
NTS305: Information Governance – managing security policies, compliance, and risk.
NTS350: Network Security Monitoring – detecting and responding to threats in real time.
NTS442: Collegiate Cyber Defense Competition – applying skills in competitive, real-world simulations.
UAT’s Network Security graduates are prepared for in-demand careers such as network security engineer, penetration tester, cybersecurity analyst, incident response specialist, and IT security auditor . These roles are critical in industries ranging from healthcare and finance to government, defense, and cloud technology.
Cybersecurity is one of the fastest-growing fields worldwide, with job demand far outpacing supply. A Network Security degree from UAT not only provides the technical expertise employers are looking for, but also ensures students graduate with hands-on experience, industry certifications, and proof-of-concept projects that showcase their ability to solve real-world problems. This makes UAT graduates uniquely equipped to protect data, strengthen systems, and shape the future of cyber defense.
Q1: Do I need to know a lot about computers before starting this program?
No prior expertise is required. UAT starts with the fundamentals and builds up, so whether you’re brand new or already tech-savvy, you’ll find the right level of challenge.
Q2: What kind of person succeeds in network security?
If you’re curious, enjoy solving puzzles, or like the idea of protecting others, you’ll fit right in. Persistence and attention to detail are often more important than prior technical skills.
Q3: Will I get real-world experience while studying?
Yes. UAT emphasizes hands-on learning, with labs, simulations, and even competitions where students defend systems against live cyberattacks. These experiences prepare you for the workforce.
Q4: How expensive is it to study network security at UAT?
UAT offers financial aid for qualifying students, including scholarships and grants. Advisors can walk you through your options to make sure your education is as affordable as possible.
Q5: What’s campus life like for someone studying cybersecurity?
You’ll join a creative, tech-focused community where students collaborate on projects, compete in cyber defense challenges, and share a passion for technology and problem-solving.
Q6: Can I study online if I can’t always be on campus?
Yes. With UAT’s flexible learning model, you can choose on-campus, online, or a mix of both, making it easier to balance your studies with other commitments.
UAT’s Network Security degree blends theory, hands-on labs, and cyber competitions to equip you with the skills to defend networks, protect data, and stay ahead of digital threats.
📍 Tempe, AZ — Real skills. Real impact.
💻 Start defending the digital world at UAT

On the 6th day of Techmas, we’re celebrating University of Advancing Technology's (UAT) six top blogs of 2025! From Artificial Intelligence (AI) art reaching the Moon to award-winning hackathon wins, immersive experiences at CactusCon, Student Innovation Projects (SIP), esports community highlights, and top Niche rankings, these stories showcase the creativity, skill, and innovation that make UAT students stand out.
1. Hacking, Learning & Networking: CactusCon 2025 By Avery Willets
UAT student Avery Willets describes his experience at CactusCon 2025, where they explored cutting-edge cybersecurity tools, attended talks on red-team tactics and hash-cracking, gained leadership insights, and connected with Arizona’s vibrant cyber community.
2. Spring Innovations Unleashed: Highlighting the Spring 2025 Student Innovation Projects By Katy Toerner
Spring 2025 Student Innovation Projects Spotlight, featuring tools and games that push creative and technical boundaries—from a 3D-to-2D animation converter to an immersive RTS game and a customizable audio plugin—showcasing the innovation driving UAT students’ work.
3. UAT Student's AI Art makes its way from Times Square to Space! By Katy Toerner
UAT student Vanessa Camacaro's AI-generated artwork — previously displayed in Times Square — was launched into space aboard the Firefly Blue Ghost Moon Lander aboard a SpaceX rocket, landing on the Moon at Mare Crisium on March 2, 2025. The piece, “La Vie En Rose,” will become part of a lunar museum — marking an extraordinary blend of AI art, human creativity, and space exploration.
4. Wyverns Gaming & Esports Club By Jayce Jakubowski
UAT’s Wyverns Gaming & Esports Club, one of the campus’s largest student groups, offering a welcoming space for both competitive players and casual gamers. Focused on community, stress relief, and connection, the club gives students a fun, supportive outlet to unwind, build skills, and get involved in campus life through gaming.

5. UAT Ranked among the Best: A top choice for Design, Safety, and Student Life By Katy Toerner
UAT’s strong performance in the 2025 Niche rankings — including being named #1 in Arizona for Computer Science and #1 in Arizona for Design.
It also notes other high ranks: #2 in the state for Information Technology, #2 for dorm quality, #3 for student life and campus safety, and top spots for food, location, and overall campus environment.
6. UAT Students win Hack The Future: Phoenix Hackathon By Robert Walker
UAT students Keegan Heaton and Ozzy James took first place at the SeedAI Hackathon in Phoenix, demonstrating their expertise in AI and cybersecurity. Their winning project highlighted real-world problem-solving skills and UAT’s focus on hands-on, practical learning.
Join the holiday tech celebration—your future in tech starts at UAT. Learn More about all UAT has to offer students today!

On the fourth day of Techmas, University of Advancing Technology's (UAT) Cyber Security Faculty are here to help you stay safe online this holiday season! From phishing scams disguised as festive deals to Wi-Fi risks while shopping on the go, the digital world can be just as tricky as it is convenient. That’s why they have rounded up their favorite tips to protect your data, devices, and digital identity—so you can focus on the joy of the season without worrying about cyber Grinches.

Dr. Briant Becote "Use Multi-Factor Authentication (MFA) whenever possible- it helps ensure your accounts are protected, even if your passwords are compromised."

Professor Aaron Rodriguez "Password managers might not be flashy, but your wallet will definitely appreciate the extra protection. Secure your accounts - secure your cash."
.jpg)
Professor Sarah Bunce "Use a password manager to have separate passwords for each of your accounts. Reused or weak passwords is one of the most common ways attackers steal your information."

Professor Adam Zeiner " Avoid Public Wi-Fi for Shopping: Never enter passwords or credit card numbers while on free Wi-Fi at a cafe, airport, or hotel. Hackers on the same network can "sniff" this traffic."
Keep the Techmas spirit going! 🎄 Apply to UAT today and start unwrapping your future in tech.

Happy National Computer Security Day! To celebrate this, we are going to go over 4 tips and why they are important to keep your computer safe. We when we look at risk, one of the biggest indicators is what websites you go to and files that are downloaded. This is because when you visit a new website or download a file you add new unknown factors that could be malicious.
First, we are going a website called virus total (https://www.virustotal.com). To scan a new website, you are going to click the “URL” tab and apply enter the website into the URL box. If you have a file that you want to make sure is safe you can click the “File” tab and select the file you want to analyze. After that what this website will do is run it through multiple security vendors detection for free. If that security vendor doesn’t detect anything it will have a green checkmark. If that security vendor detects something malicious it will provide a red explanation point. For a quick reference you will be able to see the top and are looking a full green circle indicating no malicious activity was detected.
The next common issue that can happen is having outdated software updates. Updates not only add new features to software they also include updates to security for the software. This is because people are finding new ways to break software and gain access to computer so developers will have to fix these issues though software patches. One of the most important software to update on your computer is your operating system and your web browser. The good news your operating system will automatically update on its own. For your web browser this can generally be done by going the help section at the top and then clicking the update button.
Another tip to make your computer more secure is uninstall programs that you don’t use. This is because the more programs you have on your computer the more likely one could have a security flaw that could compromise your computer. This concept is referred to attack surface where you reduce the openings for attacks. The benefit to this tip is that it will also improve the performance and free up some storage.
The last thing that is vulnerable to cyber-attack is you the person reading this. Instead of using a technology to break into your computer some people will try to email or call you to try to convince you to let them into your computer. The first defense against this is taking time and not rushing on making a decision. The next defense is getting someone else opinion since they will be able to help you determine if something is a scam or not.
Secure your future—literally. Check out UAT’s Cyber Degrees.

When it comes to cybersecurity, the pressure is real, the stakes are high, and only the sharpest digital defenders rise to the challenge. This fall, University of Advancing Technology’s (UAT) Cyber Ninjas stepped confidently onto the virtual battlefield of the National Cyber League (NCL)—a nationwide competition that tests the skills, strategy, and grit of the next generation of cyber professionals.
NCL is a nationwide cyber competition where teams compete against each other to solve as many cybersecurity-related puzzles as possible. The NCL provides numerous puzzles that can be solved in any order, covering many topics in cybersecurity, including open-source intelligence (OSINT), cryptography, password cracking, scanning and reconnaissance, wireless access exploitation, web application exploitation, enumeration and exploitation, log analysis, and forensics.
The Ninjas began training for the competition this summer by working through the NCL provided practice 'gyms' that provided dozens of practice questions that are easier than the ones that will appear in the actual competition. They also utilized other practice platforms including TryHackMe.
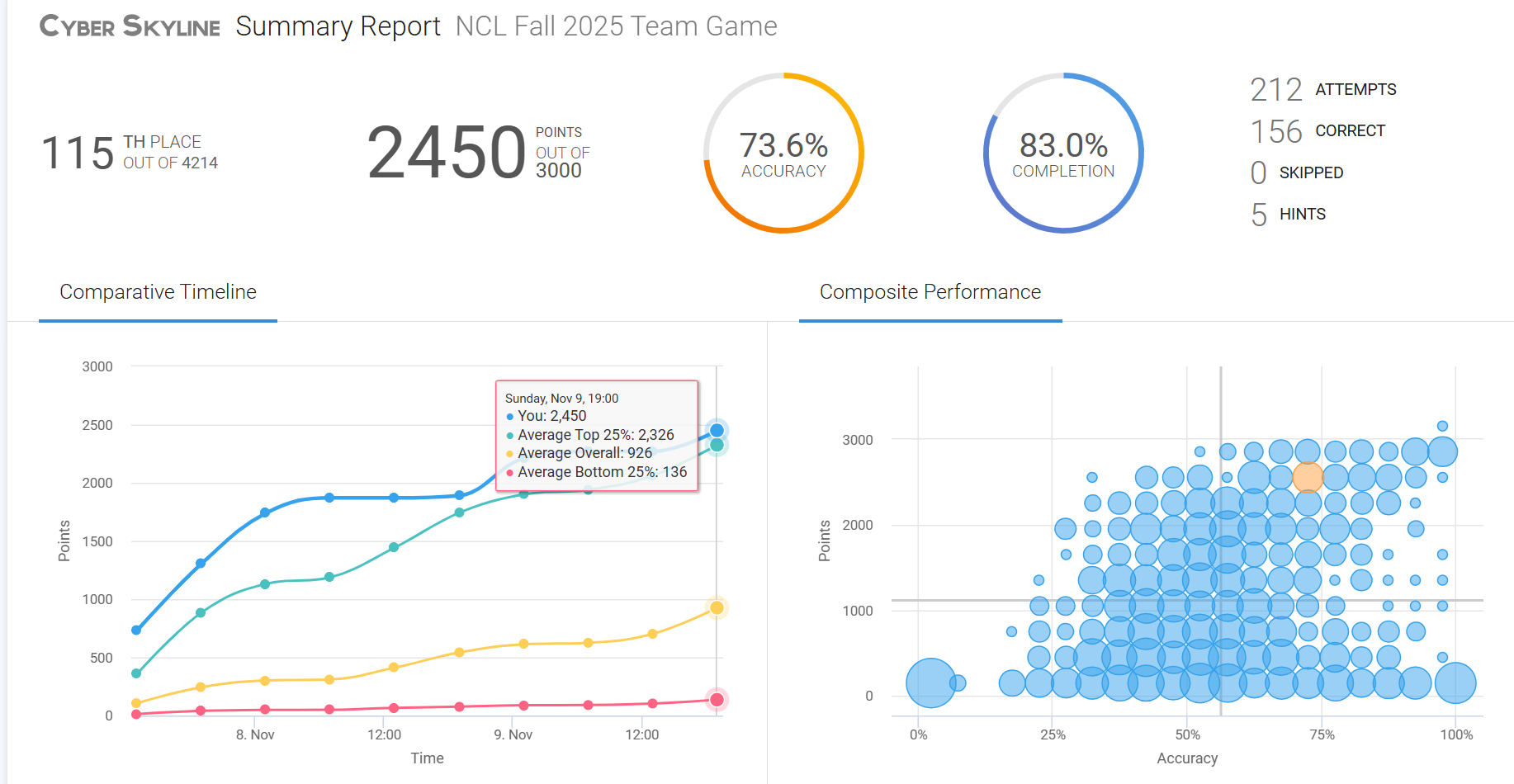
This year's competition included 4,100 teams with each team having a maximum of 7 members. Every puzzle solved gives the team a number of points based on the difficulty of the puzzle with a range from 10 to 60 points. When it came time for the actual competition, the UAT Cyber Ninjas came prepared. As a result of their hard work, the Ninjas finished in 115th place with a total of 2450 points out of a maximum 3000. They bested their last years completion of 73% by completing 83% of the 2025 competition.
This year's team consisted of Boone Stewart, Jason McDaniel, Jayse Monty, Daniel Drljaca, and Nicholas Honkus. They also received help from other UAT students Dylan Maxwell and Keegan Heaton, as well as UAT Alumnus and 2024 Valedictorian Ozzy James.
UAT couldn’t be more proud of the Cyber Ninjas and the way they represented the university throughout the National Cyber League competition. Their grit, collaboration, and technical excellence shined from start to finish, showcasing exactly what it means to be a UAT innovator and problem-solver. This team not only demonstrated their individual talent but also embodied the spirit of our cyber community—driven, curious, and ready to defend the digital world. Their performance reflects the strength of UAT’s cybersecurity programs and the bright future ahead for every student who steps into the arena.
Think you’ve got what it takes? Check out UAT’s cybersecurity programs and get started on a hands-on, challenge-driven cyber education.

Every October when Cybersecurity Awareness Month arrives it can feel like a steady stream of reminders:
Those reminders are important, but they fail to capture everyday moments where security matters the most. In my work as a security analyst, I have learned many tools to combat cyber threats. Parenting four daughters has taught me something entirely different: Practical safety grows from conversations, small rituals, and the way we treat each other when mistakes happen. This piece is about that quieter work.
Private moments that changed my view:
One night I observed my daughter Ellie, hunched over a laptop, twenty tabs open, each promising an answer. The first tab offered a free copy of a textbook. It was the top result – surely a promising solution!
I realized something in that moment. Technical advice rarely reaches people when they are exhausted or pressed for time after a long day of classes or work. The tools and rules exist but are only helpful if they fit into real life, into shortcuts and deadlines, into the small decisions people make while juggling work and family.
Zoie came to me one night asking why a friend had suddenly disappeared from a group chat. She showed me screenshots of messages that looked like account recovery prompts. We walked through the messages together and discovered subtle changes in tone and punctuation that revealed a scam. She was relieved to understand what had happened. She was also quietly proud that she had not reacted by handing over credentials. Those small wins are more powerful than any presentation slide.
From analyst to parent, and what both roles teach me:
Working as a security analyst gave me a map of threats, attack chains, and mitigation strategies. It taught me to look for patterns and to assume adversaries will probe the weakest link. But being a dad refined that map. It taught me how fatigue, embarrassment, curiosity, and convenience shape behavior. It taught me that people do not act in the sterile conditions of lab exercises. They act while caring for younger siblings, rushing to a meeting, or trying to meet a deadline. They act while trying to help a parent or keep a promise.
My parents recently offered a different perspective. I call Mom when I need to slow down and explain things simply. She asks direct questions that cut through jargon. My father asks about the practical outcomes. When I walked my father through how to spot a fraudulent phone call, he said, I wish someone had shown me this years ago. His response reminded me that security advice must be approachable for everyone, not just those comfortable with technology.
My older brother is the kind of person who believes most problems can be solved by asking the right neighbor. He is skeptical of doom-laden headlines and helpful in pointing out when I am overcomplicating a message. His input keeps my language grounded. When I craft tips for students or families I imagine explaining them to him over coffee. That mental audience makes the advice practical.
%20(1200%20x%20800%20px)%20copy%204.jpg)
Simple rituals that actually work:
I have learned that a few predictable habits can reduce a lot of risk. Each Sunday evening I sit with a cup of tea, check for software updates, look at account activity, and confirm backups are running. The ritual takes about fifteen minutes, and it buys calm for the week ahead. It is not dramatic. It is not heroic. It is reliable. I teach this to students not as a strict rule, but as an invitation. Build a ritual that matches your life and your rhythm.
Using unique passwords for each account became feasible for me the day I adopted a password manager. I still remember the first breach notice I received for a service I rarely used. Because I did not reuse credentials, the breach was an inconvenience not a crisis. That feeling of containment is worth the small effort of adopting one secure tool.
When I work with families, I emphasize pauses. Teach kids and colleagues to pause before clicking. Take one breath. Verify the sender. Ask a trusted person. The single act of stepping back interrupts the reflexive click and often prevents harm. Pauses are small and humane. They respect that people are busy and human.
Teaching without shame:
When a student admits they clicked on a phishing link, I respond with a clear recovery plan and an invitation to learn. Shame silences people and prevents the important conversations that follow mistakes. I encourage students to treat incidents as case studies that can be deconstructed without judgment.
I also bring my security analyst stories to class, not as proof of expertise, but as lived examples. One time an alert in a corporate environment pointed to irregular login attempts from a foreign country. We tracked the pattern and found a reused password across a poorly secured service. That incident became a teaching moment, a story about habits rather than villains. Students remember the narrative and the recovery steps more readily than a list of technical controls.
Conversations at home:
My daughters have taught me how to adapt conversations to age and temperament. With Samantha, the oldest, the conversation is about privacy and reputation because she is navigating professional and academic spaces. With Zoie I emphasize skepticism, spotting inconsistencies in messages, and validating sources. Ellie enjoys gaming communities, and our conversations focus on account controls and healthy boundaries. Daymi, younger and curious, benefits from gentle rules and clear explanations about what sharing means in a public space.
It helps to begin as a dialogue with a question. No lectures. I ask what they saw, what surprised them, and what felt uncomfortable. Those questions open discussion and promote cyber safety from curiosity rather than fear. When my daughters come to me with a confusing message or a new app request, we sit together, and we discover together. The search and the discussion teach them how to think about risk.
Supporting older relatives:
My parents call me when they are unsure about a banking email, a caller claiming to be from a utility, or a message that demands immediate action. I cannot assume they adopt every technological control I recommend. Instead, I focus on a few essential protections and on ways to make verification easy.
One night, a caller asked my mother for personal details to correct a records problem. She called me. I guided her through verifying the claim without giving any personal information. We contacted the official organization directly through a published number. Those steps matter because they reduce anxiety for everyone involved and preserve dignity for those who are targeted.
Recovering from mistakes:
If something goes wrong, the response matters. Quick containment, clear steps to recover, and reassurance will reduce harm. When a student in my class had their credentials stolen, we walked through resetting passwords, enabling multi-factor authentication, and reviewing account activity. We also discussed how to inform affected contacts. The immediate technical steps helped recover access. The supportive classroom response reduced the shame and encouraged others to share similar experiences.
Emotional recovery is part of resiliency too. Teach friends and family how to respond if someone is scammed. Offer help, not blame. Guide them through practical recovery steps and, when appropriate, involve financial institutions. The social response can determine whether people seek help or hide incidents out of embarrassment.
%20(1200%20x%20800%20px)%20copy.jpg)
Final thoughts:
Cybersecurity Awareness Month is a useful reminder to inspect our defaults, renew conversations, and refine our habits. It is also an invitation to treat security as a shared human project. Tools matter, frameworks matter, and so do stories. When we lead with empathy, patient explanation, and small predictable rituals, we make security part of ordinary life.
When someone slips up, respond with help, not judgment. When we teach, teach with the real rhythms of life in mind. When we design systems, design for the person who will use them while juggling work, family, and fatigue.
Security is not a test you pass once. It is a set of practices woven into daily life. It is the short pause before you click. It is the conversation with your daughter about why a message looks off. It is the call you make to a parent to verify a strange demand. It is the neighborly nudge from a brother who asks you if you are overcomplicating something. That is where meaningful safety lives.
Rather than a steady stream of cybersecurity reminders in October, we can offer a steady stream of patience and guidance in building secure practices with colleagues, students and loved ones every day.
References
National Institute of Standards and Technology. (2022). Cybersecurity awareness training impact study. U.S. Department of Commerce. https://www.nist.gov/publications/cybersecurity-awareness-training-impact-study
Verizon. (2023). 2023 Data breach investigations report. https://www.verizon.com/business/resources/reports/dbir/
Protect your future in tech — explore UAT's cybersecurity degrees today!

UAT hosted FBI Agents to discuss Cyber Security careers and pathways.
In September, the University of Advancing Technology (UAT) welcomed a special guest from the Federal Bureau of Investigation to campus. Joseph Hooper, Assistant Special Agent in Charge of the FBI’s Cyber Security Division in Phoenix, visited to share lessons learned from a recently adjudicated case and to highlight practical tips for staying safe online.
The timing of his visit was especially fitting, as October marks Cyber Security Awareness Month, a nationwide initiative to promote safe digital practices. Hooper emphasized that while threats evolve, good habits make all the difference. His key advice included:
Take a two-factor approach to everything. Strengthen your defenses with multi-factor authentication whenever possible.
Be wary of phishing. A suspicious email, text, or link could be an attempt to steal your information.
Recognize social engineering. Attackers often exploit human behavior, not just software weaknesses.
Validate identities in business. Especially in HR, in-person validation and regular audits are essential to ensure employees are who they say they are.

UAT was honored to host the FBI for this important discussion. By connecting students, faculty, and the community with experts on the front lines of cyber defense, we continue to prepare future innovators to lead the way in protecting digital spaces.
Ready to Become a Digital Defender?
Take the first step toward a cyber security career. Request information or apply today — it's quick, easy, and there’s no application fee.
Together, we can build a safer digital future. Start your journey at UAT today!

At University of Advancing Technology (UAT), Cyber Security isn’t just about textbooks and theory—it’s about collaboration, competition, and applying skills in real-world scenarios. That’s where the Cyber Ninjas come in.
The Cyber Ninjas are a student-driven cybersecurity group at UAT that brings together passionate, like-minded individuals to learn, grow, and have fun while tackling today’s toughest cyber challenges.
Alexis Sloan, a UAT Cyber Security and Technology Leadership student, explains: “The reason why I joined the Cyber Ninjas was to get more involved within the group, represent girls in the community, and work on exciting projects like the National Cyber League.”
The Cyber Ninjas compete in several competitions including:
These competitions aren’t just games—they’re opportunities to build teamwork, sharpen skills, and prepare for careers in cybersecurity.
“The best part of being in NCL is that it gives us a work-like setting. We work together to face real-life challenges in a controlled area.” – Jaylan McCoy, Network Security
Cyber Ninjas meet every Friday at 2:00 p.m. to collaborate, share knowledge, and practice for upcoming competitions. These sessions combine learning with camaraderie, creating an environment where students can experiment, fail safely, and grow stronger together.
“It enhances my education because I am able to learn how to incorporate Artificial Intelligence (AI) into Cybersecurity, and Cybersecurity into AI.” – Ozzy James, Network Security, Network Engineering, AI
Being part of the Cyber Ninjas means:
The Cyber Ninjas have combined the camaraderie of a UAT Club with the competitiveness of a team, and they welcome any and all majors to join them!
Ready to learn more about the Cyber Ninjas or UAT's Cyber Security Degree options? Request Info Today!
At University of Advancing Technology (UAT), Cyber Security Awareness month is a time where students, staff and the community gather together to share tips on making the world a better place.
October marks Cyber Security Awareness Month, and at the University of Advancing Technology (UAT), we’re diving straight into the conversation with a brand-new episode of our Tech Tangents podcast, featuring Robert Walker, Director of Community Initiatives, and Dr. David Bolman, UAT Provost.
In this kickoff episode, Robert and Dr. Bolman explore the journey of where cyber security started and how it has rapidly transformed over the years. What began as a handful of bad actors testing early networks has evolved into a landscape where AI-driven threats and the Internet of Things (IoT) have made hacking more prominent—and more dangerous—than ever before .Check out the episode in full here -
They also highlight how threat agents aren’t just virtual anymore. With the rise of interconnected devices and smart systems, cyber and physical vulnerabilities often overlap, creating new risks that demand constant awareness.
And while you’ve likely heard the classic tips—use strong passwords, enable multi-factor authentication, and keep your systems updated—Robert and Dr. Bolman stress one overlooked but critical best practice:
👉 Be mindful of what you share on social media. Posting vacation pictures in real time or broadcasting your location makes it easier for threat agents to combine digital footprints with physical opportunities. Sometimes, safety starts with silence. Check out the episode in full here -
This Cyber Security Awareness Month, join us in staying sharp, staying informed, and staying safe. Interested in starting you cyber journey, learn more about our degree options here.

University of Advancing Technology (UAT), caps off stellar camp season with annual Tech Camp with New Way Academy which gives students a technological taste of college life.
What began as a simple school partnership has evolved into a powerful annual tradition. Students from New Way Academy — a school serving bright learners who thrive in personalized learning environments — now look forward to this event as a rite of passage. For many, it’s their first time staying overnight on a college campus. For some, it’s the moment they realize they belong in the world of tech.
Each day is thoughtfully curated to provide a blend of practical skills, creative exploration, and good old-fashioned fun. UAT professors and staff lead engaging demos and workshops designed to spark curiosity and confidence. Some highlights from this year’s lineup included:
Life 101: A crash course in adulting — covering everything from budgeting and communication skills to college prep and self-advocacy.
AI Prompt Engineering: Students explored the power of artificial intelligence and learned how to craft effective prompts to generate art, text, and ideas.
LEGO Building Challenge: Creativity met collaboration as students built original structures under time pressure, solving design challenges in real time.
Robotics Challenge: Instructors introduced students to simple robotics concepts, and teams competed to complete tasks using sensors and logic.
Gameplay Testing: Students played and reviewed in-development video games created by UAT students, giving live feedback as real-world testers.

The students also had an opportunity to learn traditional art drawing and maker and fabrication techniques in building smart infrastructure.

But the learning wasn’t limited to the classroom. Campers also got a behind-the-scenes look at UAT’s cutting-edge spaces—including the Maker and Fabrication Lab, Motion Capture Studio, Art Studio, Security Operations Center, and Think Tanks—each one offering a glimpse into real-world innovation.

And of course — they didn’t go home at the end of the day. Students stayed overnight in the UAT dorms, getting a real taste of college life in a safe, supportive environment.

This partnership speaks to something greater than STEM demos and campus tours — it represents what happens when you trust students with real tools, real challenges, and real respect. Year after year, UAT and New Way Academy prove that when education is tailored to the learner, anything is possible.
We are honored to continue this decade-long tradition and can’t wait to welcome the next wave of New Way innovators.
Whether you're taking your first step into tech or you're ready to go all-in on your own innovation journey…
👉 See What You Can Study at UAT
We're the university built for future creators—and it all starts here.

University of Advancing Technology (UAT) offers a suite of Cyber Security Degrees, including Bachelor of Science Degrees in Network Engineering, Technology Forensics, Network Security and a Master of Science Degree in Cyber Security. Additionally UAT is designated as a Center for Academic Excellence by the National Security Agency in cybersecurity. The Cyber Security Faculty have a vast amount of real world experience, they are seasoned veterans in the field who are passionate about teaching the next generation of cybersecurity professionals.

Professor Becote retired from 23 years of U.S. Navy service as a Lieutenant Commander, Naval Flight Officer, in December of 2023, having served in a variety of leadership roles including Director of International Affairs: Egypt, Qatar, and Director, Tactical Operations Center for Maritime Aviation in the Middle East. His duties included technical, logistic, and operational execution spanning over 15 countries globally.
His research interests span both offensive and defensive cyber operations, focused on malware analysis, programming, wireless technology, organizational technology, and incident response. He is PMP and CISSP certified.

Professor Aaron Rodriguez is an Air Force Veteran which has served in military and contract support for various government agencies including supporting worldwide security efforts. Aaron has planned and managed Computer Incident Response Teams (CIRT) and multiple cyber training operations. He has several years of information technology background with a specialty in cyber security and information protection. Aaron graduated from Grand Canyon University with a Bachelor's in Information Technology and a Master's in Cyber Security and Information Assurance.

Dan Wilkins has over 30 years of experience in Computer and Information Security Industry. He is an Army Veteran and has served in military and contract support positions for various government agencies including worldwide security efforts. Dan has planned and managed Computer Incident Response Teams (CIRT), Computer Forensics, Red team / Blue team exercises and multiple cyber scenarios including Industrial Control Systems and SCADA systems. He has GRC experience with International and U.S. based security legislative requirements and standards. He has served in various information security positions throughout his career to include: Chief Information Security Officer, IT Director, Cyber Crime analysis and response; Security Consultant; and Senior Cyber Security Engineer.
Dan is a 5 time author with International book publications, a business owner, and he has an art gallery with numerous original oil paintings.

I am a proud father of 4 girls and have one grandson. One of my hobbies is collecting Funko Pop’s and I am also into anime (totally Otaku!). I am originally from Arizona, but I lived in Seattle for the past 5 years. I have a Bachelor of Science in Information Technology and Master of Science from the University of Phoenix. I am currently going to school for my PhD in Management with a focus on Information Systems.
Learn More about UAT's Cyber Security Degrees Today!

Last week, University of Advancing Technology (UAT) proudly hosted the FBI Cyber Academy—a dynamic, hands-on camp where high school students dove headfirst into the world of digital forensics and cyber investigations. This immersive program, held on UAT’s Tempe campus, brought together students, FBI professionals, and UAT’s own faculty and Cyber Ninjas to deliver an unforgettable week of education and inspiration.
Throughout the weeklong academy, high school students engaged directly with FBI special agents, evidence technicians, intelligence agents, and cyber experts, gaining firsthand knowledge of how real-world cyber investigations unfold. In addition to FBI professionals, UAT faculty and students helped guide the experience, offering mentorship and instruction in both technical and investigative skills.

Students stayed on campus in Founder's Hall, getting a taste of college life while working on their biggest challenge of the week—a mock criminal case. Divided into investigative teams, students conducted interviews, analyzed digital evidence, and employed forensics tools to build their case. They worked tirelessly to track digital footprints, piece together clues, and prepare a presentation for a mock indictment. The camp culminated in a simulated courtroom session where students presented their evidence before a real U.S. Attorney, arguing for an indictment based on the case they built.
The success of the program was made possible in part by UAT’s dedicated Cyber Ninjas—Ozzy James, Alexis Sloan, Boone Stewart, and Keegan Heaton—who volunteered their time and expertise to mentor the students throughout the week. Their guidance played a crucial role in helping the participants navigate complex digital challenges and understand the fundamentals of cyber investigations.

As a special reward for their hard work and achievement, each student who completed the FBI Cyber Academy has been offered UAT’s Futurist Scholarship, contingent upon their acceptance to the university. This opportunity opens a direct path for aspiring cybersecurity professionals to continue their education and launch careers in this vital field.
The FBI Cyber Academy at UAT not only introduced students to the fascinating world of cybercrime investigation but also showcased the collaborative spirit and forward-thinking environment that defines UAT. With initiatives like this, the future of cybersecurity is in good hands.
UAT is designated as a National Center of Academic Excellence in Cyber Defense (CAE-CD) by the National Security Agency (NSA).—giving you a proven foundation to build your career.
👉 Check out our Cyber Security degrees. Apply now or schedule a campus tour to see where your cyber journey begins.

From June 23rd to 27th, University of Advancing Technology (UAT) transformed into a technological playground of possibility for 13 curious minds, ages 5 to 16, during our first-ever Future Innovators Day Camp.
Throughout the week, our campus buzzed with the sound of discovery, laughter, and the occasional robotic beep as campers explored everything from artificial intelligence to drone design. While this was UAT’s debut day camp for K–12 students, it certainly won’t be the last.
Each morning began with excitement and anticipation as campers arrived on campus ready to explore a new STEM adventure. The days were thoughtfully structured around themes that blended technology, creativity, and hands-on learning. On Day 1, campers dove into the world of Drones & Robotics, programming Sphero robots and navigating custom-built mazes. Day 2 introduced them to the thrilling realm of Cybersecurity, where they created strong passwords and tried their hand at safe hacking simulations.

By midweek, the energy reached a high as campers built their own games and teamed up for a mini Game Jam during Game Design & Virtual Reality day. Laughter filled the labs as pixelated dreams came to life on-screen.

Day 4 took a deep dive into the future with AI & Coding. Campers trained their own AI models and explored how machines learn and make decisions. On the final day, imaginations soared in 3D Modeling & Digital Art, where campers created original characters in TinkerCad and animated them with Mixamo.
But the learning wasn’t limited to the classroom. Campers also got a behind-the-scenes look at UAT’s cutting-edge spaces—including the Maker and Fabrication Lab, Motion Capture Studio, Art Studio, Security Operations Center, and Think Tanks—each one offering a glimpse into real-world innovation.

Beyond the tech, there was time for some classic camp fun—friendly games of ping pong, impromptu chess matches, and a strong sense of community that grew with each passing day.

Every afternoon closed with a student showcase, where proud parents gathered to witness the projects and presentations their campers created. From robot demos to animated characters, each showcase was a celebration of effort, imagination, and growth.
We’re just getting started.
The Future Innovators Day Camp returns in Summer 2026, and we’re launching a brand-new Overnight STEM Camp for high school students. Think late-night game builds, collaborative tech projects, and a taste of college-level learning at UAT.
Who can attend the camp?
Children ages 5–16 with an interest in STEM, tech, and hands-on learning.
Do campers need prior experience with coding or robotics?
Not at all! All skill levels are welcome—from curious beginners to budding engineers.
What should campers bring?
A water bottle, closed-toe shoes, and curiosity. All tech is provided by UAT.
Are meals included?
Yes. Lunch and snacks are included each day.
Will there be a camp in 2026?
Yes! Day Camp will return, and a new Overnight STEM Camp for high school students is in the works.
Where can I learn more about UAT programs?
Right here: Explore UAT Degrees
Whether your child is taking their first step into tech or you're ready to go all-in on your own innovation journey…
👉 See What You Can Study at UAT
We're the university built for future creators—and it all starts here.

At the University of Advancing Technology (UAT), we believe that innovation isn’t just about technology—it’s about people. This past Saturday, UAT Cyber Security student, Alexis Sloan, exemplified that belief when she volunteered her time and talent to teach senior citizens the basics of IT at a local church in Phoenix, Roeser Church of Christ.
With support from UAT’s Community Initiatives department, Alexis quickly answered a request for help by preparing a personalized tech session for 11 local seniors. Equipped with a handout she created herself, Alexis taught attendees how to navigate their tablets, recover accounts, and identify whether websites were safe—all while fostering meaningful conversations around online privacy and general location sharing.
Each participant had their own device, and Alexis made sure every question was met with patience and respect. “They were so nice and really patient,” Alexis shared. “I had some free time and thought it sounded like fun—and it really was!”
This event wasn’t just about learning how to swipe or tap; it was about building confidence in a digital world. And thanks to UAT’s swift coordination and commitment to service, Alexis was empowered to turn her knowledge into impact.
UAT’s Community Initiatives department proudly facilitated this opportunity because we understand that true leadership means stepping up, showing up, and giving back. We are proud to support students like Alexis who carry our mission into the real world—where technology meets compassion.

At UAT, we don’t just prepare students for careers—we prepare them to serve, lead, and innovate with honor. Our foundation is our community, and with every small act of service, we’re building a stronger one together.
Join UAT’s Journey and Learn More today.

Originally Published On Cybersecurity Insiders
Artificial intelligence (AI) is transforming the tech world—but not just in ways you might expect. While it’s powering everything from smart assistants to self-driving cars, cybercriminals are also using AI to launch smarter, faster, and more targeted attacks.
If you’re even thinking about a future in cybersecurity, ethical hacking, network defense, or emerging tech, here’s a real-world look at why your skills will matter more than ever—and how hackers are already using AI to try and stay one step ahead.
Gone are the days of obvious “Nigerian prince” scams. Today’s phishing emails are written by AI that can sound like your professor, boss, or even a family member—crafted using info pulled from your public social media accounts.
AI can now clone voices and faces. That’s right—deepfake videos and audio can impersonate people you trust, tricking you into clicking bad links or sending sensitive info. It’s not sci-fi anymore. It’s real—and it’s happening now.
Hackers are using AI tools like WormGPT to code malware that learns as it spreads. These programs can rewrite themselves to avoid detection, automate attacks, and adapt to different security systems.
As a future cybersecurity pro, your role won’t just be reacting to these threats—you’ll be anticipating them. Here’s what you can start doing today:
Use Multi-Factor Authentication (MFA)
Think of it as your digital seatbelt. Even if your password gets leaked, MFA helps keep your accounts safe.
Be Suspicious of “Too Good to Be True”
If an email seems off, don’t click. Hover over links. Verify senders. Trust your instincts—and double-check everything.
Limit What You Share
Your TikTok, IG, and LinkedIn bios can give hackers clues. Set your accounts to private and keep the oversharing in check.
Learn the Tech Behind the Threats
The best way to fight back? Understand how these systems work. That’s where your future education comes in.
Cybercriminals are evolving—and the world needs digital defenders who can stay ahead. At University of Advancing Technology (UAT), we don’t just teach you theory. You’ll build real-world skills in ethical hacking, network defense, and AI-driven security. Your classroom is the front line.

Every graduating class has its standouts—students who go above and beyond in their academics, involvement, and personal growth. For University of Advancing Technology's (UAT) Class of 2025, that standout is Ozzy James, graduating with three Bachelor of Science degrees in Network Security, Network Engineering and Artificial Intelligence (AI). Ozzy not only mastered the classroom, but also embraced every challenge, built a strong community, and remained true to his values.
When asked how he maintained academic excellence throughout his time at UAT, Ozzy’s answer was immediate and heartfelt: connections. “Having really good connections with friends and family, and strong faith in my beliefs—those were everything,” he shared. “They helped me through the tough times and reminded me to focus on myself. When I stopped taking care of myself, everything else started to fall behind.”
This balance—between academic dedication and personal well-being—proved to be the secret to his success. His cyber team, professors, and loved ones became his foundation, helping him stay grounded while reaching for big goals.
Two professors stood out as transformative influences: Professor Aaron Rodriguez and Dr. Briant Becote. “Professor Rodriguez was incredible. I had him for Personal Identification and Security—one of my favorite classes,” Ozzy recalled. “He’d sit down with us and make sure we really understood the material, and if he saw anyone struggling, he’d check in right away.” Then there’s Dr. Becote, who helped launch the UAT Cyber Ninjas team, which Ozzy now leads. “I met him in my CCDC class—Collegiate Cyber Defense Competition—and that’s where I really got into the hands-on side of ethical hacking. It’s something I’d always wanted to do, and he brought more and more of that to the school.”
College wasn’t without its challenges. The most difficult moments came when major projects like SIP (Student Innovation Project) and boards collided with regular coursework—and a job on top of that.

“It was overwhelming,” Ozzy admitted. “But leaning on my support system, especially professors like Dr. Becote and Professor Rodriguez, and just talking things out with friends—that helped a lot. Finding small ways to stay grounded made a big difference.”
What helped him the most? Learning that constantly grinding wasn't sustainable. “Focusing only on school put me in a bad mental space. Once I started putting more time into my faith, my family, and just giving myself a break, everything else started to fall into place.”
One of the biggest surprises during Ozzy’s college journey was personal growth—especially in confidence and communication. “In high school, I didn’t go out much. I didn’t really network or connect beyond my circle. But at UAT, my friends and professors pushed me to go to conferences like CactusCon, meet Arizona’s CISO, and attend AI talks and robotics events. That changed everything.” These experiences opened new doors—not just professionally, but socially and personally. “I’ve made so many connections, in cybersecurity and outside of it. It’s helped me see all the different aspects of this field.”

Post-graduation plans are still evolving, but Ozzy’s vision is clear: he wants to continue building community. “I’m looking for a job where I can do what I’ve done here—help others grow, stay connected, and raise awareness about cybersecurity threats. I want to keep leading, keep learning, and keep giving back.” In five to ten years, he sees himself still learning, and still deeply embedded in his field. “I love learning. I’ve always loved learning. Whether I’m leading a corporate team or mentoring students at a school, I just want to keep growing and helping others do the same.”
Ozzy’s advice to underclassmen and incoming students? Don’t make college only about school. “If you focus only on your studies, you’ll burn out. But if you focus only on having fun, you’ll miss the point. The key is balance—school, self-care, family, faith, and fun. When you find that balance, everything else starts to work.”
When Ozzy found out he was chosen as Valedictorian, it was a complete surprise. “I never aimed for recognition. I just wanted to do my best and learn everything I could. So finding out that my professors chose me to represent the class—it’s incredibly humbling. I honestly didn’t even know they voted on it,” he laughed. “But it feels amazing to know they believed in me.” Ever humble, he adds, “I think everyone’s hard work should represent our class, not just mine. But I’m honored.”
Congratulations Ozzy, we are so proud of you and can't wait to see what you accomplish in your future.
Learn more about how to get your UAT journey started today!

At University of Advancing Technology (UAT), the Cyber Ninjas competition team stands as a cornerstone of our cybersecurity community. We're more than just a club—we are a diverse group of passionate students united by our love for cybersecurity, dedicated to skill development, and committed to creating an inclusive environment for newcomers and veterans alike.
The UAT Cyber Ninjas welcome all students, regardless of their experience level. Whether you're taking your first steps into the world of cybersecurity or you've been breaking and defending systems for years, our team has a place for you. Our strength lies in our collaborative approach—experienced members regularly mentor newcomers, and everyone is encouraged to reach out to our Professors & Subject Matter Experts, Dr. Briant Becote and Aaron Rodriguez when faced with challenging problems.
Our training methodology centers around self-paced learning through the National Cyber League (NCL) Gymnasium and TryHackMe modules, which allows each member to progress according to their individual skill level and interests. This personalized approach ensures that everyone continues to grow their cybersecurity knowledge regardless of where they started. We also take knowledge learned in our amazing classes and apply it to the team and competitions.

The Cyber Ninjas participate in numerous competitions throughout the year, spanning both offensive and defensive cybersecurity domains. Our comprehensive approach includes competing in National Cyber League, Google CTF, Buckeye CTF, and Cat the Quest. Here, we hone our system exploitation, OSINT, and password cracking skills. On the defensive competitions, we regularly participate in the Collegiate Cyber Defense Competition (CCDC) and National Centers of Academic Excellence in Cybersecurity (NCAE) Games, where we focus on protecting networks and systems from active threats.
This balanced participation in offensive and defensive competition gives our members a holistic cybersecurity skillset. The challenges we face—from identifying vulnerabilities to implementing robust security measures—mirror real-world scenarios that cybersecurity professionals encounter daily. Many of our competitions involve time pressure elements that simulate the urgency of actual security incidents, preparing our members for future careers.
What makes these competitions particularly valuable is their global nature. By competing against teams from various backgrounds and expertise levels worldwide, our members gain exposure to diverse approaches and techniques. These international connections often lead to networking opportunities and knowledge sharing that extend beyond the competitions themselves. Therefore, creating a richer learning environment for everyone involved.
Our commitment extends beyond competitive events. The Cyber Ninjas actively engage with the broader cybersecurity community through various professional development opportunities throughout the year. We regularly attend industry conferences like CactusCon, where members network with security professionals, participate in workshops, and gain exposure to cutting-edge security research. These conferences often lead to internship connections and mentorship opportunities that help launch our member's careers.
The team also organizes and attends professional networking events that bridge the gap between academic learning and industry practice. These connections have proven invaluable for members seeking to understand current market demands and career pathways.
Recently, we had the privilege of meeting with Ryan Murray, Arizona's Chief Information Security Officer, to discuss the state's cybersecurity posture, AI integration in security operations, and valuable career guidance. These professional development opportunities provide our members with industry insights and connections that complement classroom learning, creating a more comprehensive educational experience. Meeting with industry professionals gives our members a clearer understanding of career pathways and current cybersecurity challenges, helping to bridge the gap between academic theory and real-world practice.
What truly sets the Cyber Ninjas experience apart is the lifelong connections formed while tackling complex challenges. When you join our team, you don't just gain technical skills—you build a professional network and friendship circle that extends far beyond graduation. Our members regularly describe the team as "finding their people" at UAT. The camaraderie developed during late-night competition preparations, celebrating victories at our traditional post-competition Sonic runs, or sharing a team Thanksgiving dinner creates bonds that last throughout your academic journey.
On campus, you'll often find Cyber Ninjas gathered in the Security Operations Center (SOC). This hub serves as our training ground, meeting space, and occasional movie theater where we combine relaxation with research during our regular movie nights. These informal gatherings help strengthen our team bonds while providing a casual space to discuss security concepts in a relaxed setting.
We pride ourselves on maintaining an open, supportive environment where anyone interested in cybersecurity can find their place. Whether you're looking to compete, learn new skills, or simply connect with like-minded tech enthusiasts, we invite you to be part of our journey in the ever-evolving world of cybersecurity.
Ready to step into the digital shadows with the Cyber Ninjas? Find us in the UAT SOC or connect with any team member—your journey into the fascinating world of cybersecurity begins with us.

University of Advancing Technology (UAT) has achieved impressive standings in the 2025 NICHE rankings, reflecting its commitment to excellence across various degrees and college experiences.
#1 Best College in Arizona for Computer Science
UAT has been honored as the #1 Best College in Arizona for Computer Science by Niche for the second consecutive year. This recognition underscores the university's dedication to providing cutting-edge education in computer science, preparing students to excel in a rapidly evolving field.
#1 Best College in Arizona for Design
Creativity and innovation are at the heart of UAT's design programs, leading to its ranking as the #1 Best College in Arizona for Design. Students have the opportunity to explore various design disciplines, from Game Design to Advertising Art, fostering a versatile skill set.
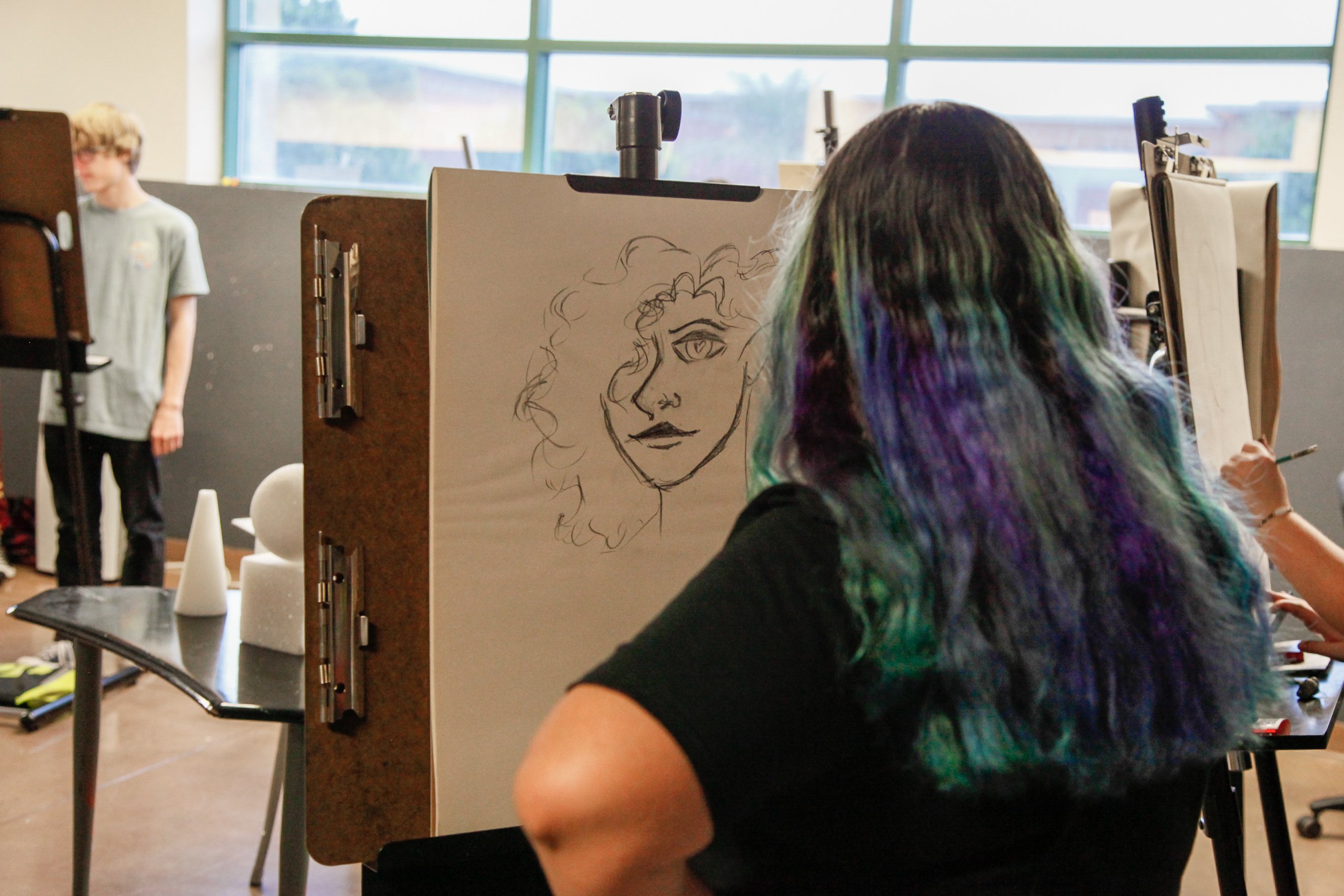
#1 Best Fully Online College in Arizona
UAT's 20+ degrees are all offered fully online allowing more students to access the excellence and innovation UAT has to offer. UAT recently revamped the Online format giving student more time to focus on mastering their coursework, staying on track for graduation, and ultimately achieving their academic goals with greater confidence and support.
#2 Best College in Arizona for Information Technology
Recognized as the #2 Best College in Arizona for Information Technology, UAT offers a suite of Cyber Security degrees including Bachelor of Science degrees in Network Engineering, Network Security, Technology Forensics, and a Master of Science degree in Cyber Security. UAT Is designated as a National Center for Academic Excellence (CAE) in Cybersecurity by the National Security Agency (NSA).

#2 Best College Dorms in Arizona
UAT’s Founder's Hall has been recognized as one of the best college dorms in Arizona, earning the #2 spot on Niche’s “Best College Dorms in Arizona” list two years in a row. This ranking reflects our commitment to providing students with a safe, modern, and comfortable living environment that enhances their campus experience. From suite-style rooms to an updated kitchen, collaborative community spaces like Tech Tanks and the streaming suite—UAT’s housing is not only steps to a few minutes walk from classrooms, cafe, and restaurants, and more, it's designed to support both technology-driven learning and a vibrant student life.
#3 Best College in Arizona for Student Life
UAT's vibrant campus life has earned it the #3 position for Student Life in Arizona. With a plethora of clubs, events, and networking opportunities, students can engage in a community that supports both personal and professional growth.

#3 Safest College Campus in Arizona
Safety is a top priority at UAT, leading to its ranking as the #3 Safest College Campus in Arizona. The university's commitment to maintaining a secure environment allows students to focus on their studies and campus activities with peace of mind.
#4 Best College in Arizona for Food
UAT's Cafe has been recognized as the #4 Best College in Arizona for Food. Offering a variety of nutritious and delicious options, the university ensures that students have access to meals Morning, Noon, Night and Late Night!

#4 Best College Location in Arizona
Situated in Tempe, UAT boasts the #4 Best College Location in Arizona. The campus's proximity to tech hubs, cultural attractions, and recreational activities provides students with a dynamic and enriching environment.
#6 Best College Campus in Arizona
UAT's commitment to providing a conducive learning environment is reflected in its ranking as the #6 Best College Campus in Arizona. From the Security Operations Center (SOC) to the Digital Maker Lab, UAT offers access to advancing technology to their students 24/7.

#6 Colleges with the Best Professors in Arizona
The dedication and expertise of UAT's faculty have earned the university the #6 for Colleges with the Best Professors in Arizona. UAT hires industry expert faculty to teach the next generation of technology professionals.

Learn more about all UAT has to offer today!

University of Advancing Technology (UAT) Cyber Security Student Alexis Sloan attended the AZ Tech Council Event on Tuesday March 25th. She discusses the opportunities and learning experience the event brings to students.
Going to the TechFusion Conference was a priceless experience that gave profound insights into the quickly advancing world of innovation, Artificial Intelligence (AI), and cybersecurity. As an understudy, being surrounded by industry pioneers, trailblazers, and forward-thinkers provided an interesting viewpoint on the patterns forming the long-term work. One of the most impactful sessions was the AI Change Board, where specialists talked about the down-to-earth applications of AI in commerce. A key takeaway was that AI ought to be seen as a collaborative tool, not a substitute for human insights. Peter Meyers emphasized the significance of small, vital AI ventures to assist organizations in constructing confidence in deployment. UAT Professor Tony Hinton, an AI ingenious, pushed for open-source AI instruments, making a solid case for open and cost-effective development.

Cybersecurity was another significant subject, with discourses highlighting the developing role of AI in both ensuring and challenging security frameworks. The Cybersecurity Career Methodologies session underscored how organizing and leveraging abilities like item administration and information science are key for standing out within the work showcase.
For undergraduates, going to this conference was more than a fair opportunity to learn—it was a chance to interact with experts, get real-world industry challenges, and pick up career experiences. The organizing openings were invaluable, strengthening that submitting resumes alone isn't sufficient in today's competitive job advertise. Discussions with experts have given clarity on developing job roles in AI, cybersecurity, and cloud computing. Generally, TechFusion was an eye-opening experience that highlighted the significance of flexibility, ceaseless learning, and organization. For any student considering a tech career, going to such occasions may be a must—it bridges the gap between scholarly information and industry expectations, preparing us for a future driven by development.
Learn more about UAT today!