From holiday tech thrills to hands-on innovation—take the next step with UAT. Apply or inquire today!

ABOUT UAT
University of Advancing Technology is an elite, private college that serves its student body by fostering knowledge creation and academic excellence in an environment that embraces the young technophiles of the world. With three centers of research and a suite of technology-centered undergraduate and graduate degrees, the University is a recognized leader in technology education.

The Digital Maker and Fabrication Degree at University of Advancing Technology (UAT) prepares students to design, prototype, and fabricate real-world projects that bridge digital creativity and physical production. As industries demand faster innovation and hands-on problem solving, maker-focused technologists are becoming essential across tech, design, and manufacturing fields.
Located in Tempe, Arizona, UAT delivers a technology-first, project-based education built for students who want to create—not just conceptualize.
Digital Maker and Fabrication is a multidisciplinary field that combines digital design, fabrication methods, electronics, and creative technology. Students learn how to move ideas from screen to physical form using modern tools, iterative design processes, and hands-on experimentation.
This degree blends elements of engineering, digital art, industrial design, and emerging technology, preparing graduates to adapt across creative and technical industries.
Rapid prototyping, customization, and experiential design are now standard across many industries. Employers value professionals who can ideate, build, test, and refine products quickly using both digital and physical tools.
Digital maker and fabrication skills support innovation in product development, creative technology, education, entertainment, and entrepreneurship. As maker spaces, smart manufacturing, and interactive environments grow, hands-on fabrication expertise continues to gain relevance.
University of Advancing Technology emphasizes experiential learning through a technology-first curriculum. Students pursuing the Digital Maker and Fabrication Degree design and fabricate projects throughout their coursework, working hands-on in UAT’s Maker Lab with tools and technologies used for prototyping, fabrication, and iterative design. Instead of exam-only assessment, students graduate with practical experience and professional portfolios that demonstrate real-world making skills and production-ready problem solving.
Students develop adaptable, future-ready skills that connect digital tools with physical creation.
Digital design and rapid prototyping
Fabrication techniques and material processes
Electronics and interactive systems
Iterative problem-solving through making
Portfolio-driven project development
These skills prepare graduates to work across evolving creative and technical roles.
Graduates of the Digital Maker and Fabrication Degree are prepared for careers where hands-on innovation is critical. Career paths span fabrication, creative technology, product development, experiential design, education, and entrepreneurial ventures.
Opportunities are available within Arizona’s growing tech and creative industries as well as national and global markets.
1. What types of projects do students create in the Digital Maker and Fabrication degree?
Students create hands-on projects that may include prototypes, fabricated objects, interactive installations, and digitally designed physical products developed through iterative making.
2. How does the Digital Maker and Fabrication degree differ from traditional engineering or design programs?
This degree focuses on applied making and fabrication rather than theory alone, blending digital design, hands-on building, and creative technology into one integrated program.
3. What tools and technologies are used in UAT’s Maker’s Lab?
Students use a range of fabrication and prototyping tools designed to support digital making, physical production, and experimental project development.
4. Can this degree support entrepreneurial or freelance career paths?
Yes. The program emphasizes portfolio development and hands-on skills that support entrepreneurship, freelance work, and independent creative technology projects.
5. How does the Digital Maker and Fabrication degree prepare students for emerging technologies?
By emphasizing experimentation, iterative design, and adaptability, the program equips students with transferable skills that evolve alongside new tools and technologies.
If you’re ready to turn ideas into real, buildable creations, the Digital Maker and Fabrication Degree at University of Advancing Technology offers the hands-on education to make it happen.
👉 Explore the Digital Maker and Fabrication Degree
👉 Apply to UAT and start creating today

The future of technology depends on problem solvers, coders, and creators who can build innovative software solutions. Computers are integrated into nearly every part of daily life, making computer science one of the most valuable skills you can invest in. From the first tools of the past to today’s engineering marvels, technology has always shaped our world. Earning an Advancing Computer Science (ACS) degree at University of Advancing Technology in Arizona is a future-focused choice that prepares you for careers in software development, programming, and emerging technologies.
UAT’s Advancing Computer Science degree blends coding, algorithms, and frameworks with hands-on design and development. Students gain experience in mobile apps, big data, machine learning, and embedded systems, preparing them to solve real-world problems with innovative solutions. Unlike traditional programs, UAT emphasizes applied learning so graduates leave with both technical expertise and creative problem-solving skills.
UAT’s Advancing Computer Science degree stands out because it combines innovation, mentorship, and hands-on learning. Here are a few reasons students choose UAT:
Synchronic Learning Model– mentorship, collaboration, and project-based education.
Innovation Requirement– every student must create a unique, real-world project.
Hands-On Labs – work with modern tools, frameworks, and technologies.
Syncflex Learning Options– flexibility to balance education with personal goals.
Through this approach, students graduate ready to meet industry demands. Along the way, they learn to follow the software development process, code in multiple languages (Python, Java, C#), build mobile and multi-platform apps, and work with data structures, algorithms, big data, and machine learning.
UAT's Computer Science degree includes a range of courses that prepare students to work across programming, data, and emerging technologies. Some of the key classes are:
CSC202: C# Programming I – foundations of C# and object-oriented programming.
CSC203: Java Programming I – core Java concepts and application development.
CSC235: Python Programming I – essential Python skills for modern software.
CSC240: Linux Operating System – understanding and working with Linux environments.
CSC340: Big Data Essentials – fundamentals of big data systems and analysis.
CSC373: Machine Learning – introductory concepts and applications of machine learning.
These courses give students a strong technical foundation while encouraging them to apply their skills to real-world challenges.
Graduates of UAT’s Advancing Computer Science degree step into high-demand careers such as software developer, mobile app designer, data analyst, machine learning engineer, and systems architect. With problem-solving, coding, and innovation at the core of their education, students leave UAT ready to thrive in a fast-paced tech industry. An Advancing Computer Science degree not only opens the door to competitive salaries and career growth, but also equips graduates with the skills to shape the future of technology
Q1: Do I need prior programming experience to start the Advancing Computer Science degree at UAT?
No prior coding knowledge is required. UAT’s courses start with fundamentals and gradually build up, so beginners can gain confidence while more experienced students are still challenged.
Q2: What kind of student succeeds in computer science?
If you enjoy problem-solving, creativity, and working with technology, you can thrive in computer science. Curiosity and persistence are more important than having all the answers on day one.
Q3: How much math is required for computer science?
Computer science does use math, but at UAT it’s introduced in practical ways tied to coding, algorithms, and problem-solving. You’ll get the support you need to succeed, even if math isn’t your strongest subject.
Q4: What financial aid options are available at UAT?
UAT offers financial aid for qualifying students, including scholarships, grants, and loans. Admissions advisors can guide you through the application process and help you explore available options.
Q5: Is UAT an accredited university?
Yes, UAT is accredited and recognized for its specialized focus on advancing technology. This ensures your degree holds real value with employers and graduate schools.
Q6: What is campus life like at UAT?
UAT offers a collaborative environment where students work on innovative projects, join clubs, and connect with peers who share their passion for technology and creativity.
Q7: Can I take classes online or only on campus?
With UAT’s Syncflex model, students can choose a flexible mix of online and on-campus courses to fit their schedule and learning style.
UAT’s Advancing Computer Science degree equips you with coding, analytics, and machine learning skills to tackle tomorrow’s tech challenges, today.
📍 Tempe, AZ — Real labs. Real challenges. Real solutions.
💻 Begin shaping the future with UAT

UAT’s (University of Advancing Technology) Summer 2026 camps offer hands-on, future-focused STEM experiences —designed to inspire, challenge, and prepare the next generation of innovators.
Summer at the University of Advancing Technology isn’t about keeping students busy — it’s about helping them discover what they’re capable of building. In 2026, UAT is proud to offer two distinct, high-impact summer camp experiences designed for curious minds at different stages of their STEM journey.
From our K–8 Future Innovators Day Camp to our first-ever teen overnight STEM experience, these programs are built for students who want more than worksheets and lectures — they want to create, experiment, and explore the future of technology.

Now entering its second inaugural year, the Future Innovators Day Camp is a highly selective, cohort experience designed for K–8 students who are ready to explore technology in a hands-on, age-appropriate way.
This flexible, day-only camp allows UAT faculty and mentors to tailor activities based on participant age groups, ensuring every student is challenged, supported, and inspired throughout the week.

What Students Will Explore
Each day introduces a new discipline, giving campers a broad view of how technology connects creativity, logic, and problem-solving:
With small group sizes, students receive personalized attention while developing confidence, curiosity, and foundational STEM skills — all inside a university environment built for innovation.
July 20–24, 2026 | Overnight Experience | Ages 13–17
Summer 2026 also marks a major milestone: UAT’s first-ever teen overnight camp.
This five-day immersive STEM adventure is designed for incoming freshmen through graduating seniors who are ready to experience college-level technology, collaboration, and independence — all while living on campus.

Campers don’t just learn about STEM — they live it. Throughout the week, students:
Evenings bring esports competitions, team challenges, and shared downtime that turns new friends into collaborators — and the campus into a tech-powered summer retreat.
The experience culminates in a capstone presentation, where campers showcase their projects, reflect on their growth, and walk away with:
This is more than a camp — it’s a preview of what’s possible.
Whether students are just beginning their STEM journey or ready to experience life on a university campus, UAT’s Summer 2026 camps are designed to spark curiosity, build skills, and create unforgettable experiences.
This summer isn’t about watching tech happen — it’s about building it. Claim your spot in UAT’s Summer 2026 camps and start creating.
Register for UAT Future Innovator's Camp (K-8)
Register for UAT Overnight STEM Camp (9-12)
Already graduated? Learn more about how you can join UAT, schedule a tour or visit University of Advancing Technology.

The University of Advancing Technology (UAT) has achieved a ranking in Arizona's prestigous Phoenix Business Journal Best Places to Work
The University of Advancing Technology (UAT) is proud to be ranked #14 on the Best Places to Work – Small list in the December 16, 2025 issue of the Phoenix Business Journal — the highest-ranked university in Arizona on that list. This distinction reflects our deep commitment to cultivating a workplace where every member of our community feels valued, supported, and inspired.
What sets UAT apart isn’t just our reputation for academic excellence — it’s our intentional investment in people.
Over the past 12 months, we’ve significantly expanded our benefits and perks to better support our faculty and staff in ways that go beyond the typical offerings.
Partnering with a premier group discount program, we now provide employees with free perks and a comprehensive platform of meaningful savings — including discounts on gym memberships, restaurants, and more. This initiative isn’t just about benefits on paper; it’s about empowering our team to stretch their hard-earned dollars further and enjoy life both inside and outside of work.
In addition, we introduced one of the most tangible perks our employees love: unlimited meals at the UAT Café. This isn’t just about food — it’s about nourishment, convenience, and community. By removing the everyday stress of meal prep and offering a space where colleagues can gather, recharge, and connect, we’re investing in the well-being and morale of our entire community.
UAT’s benefits landscape goes beyond the ordinary with what has become one of our most cherished offerings: the Summer Happiness program.
Designed to brighten Arizona’s sizzling months, this initiative reflects our belief that work should be human first — and fun too. From early May through late August, employees enjoy:
A casual dress code every day
Weekly employee-led events that spark joy and connection
Favorites like Tie-Dye T-Shirt Day, Christmas in July (complete with festive cookie decorating), Bingo & Trivia, and Bring Your Pet to Work Day
Visits from snow cone and ice cream trucks
Catered lunches and community celebrations
A culminating Manager’s Breakfast — cooked fresh by UAT leadership for the whole campus
What makes Summer Happiness truly special is its employee-led nature. A rotating committee of staff conceptualizes and hosts events that reflect diverse personalities and passions. This ensures every summer season feels fresh, inclusive, and genuinely fun — strengthening bonds, celebrating individuality, and reminding us all why UAT is such a uniquely positive place to work.
UAT isn’t just a place you work — it’s a place you belong, grow, and thrive. Being the highest-ranked university on Arizona’s Best Places to Work list demonstrates our commitment to the people who make our mission possible: passionate educators, innovators, mentors, and creators.

With the world more interconnected than ever, threats to personal and organizational data have grown in number and complexity. The digital world needs skilled defenders who can safeguard online interactions for individuals, businesses, and governments alike. Network security is the foundation of this protection, providing the tools and strategies to detect attacks, defend systems, and ensure safe digital operations. At University of Advancing Technology (UAT), the Network Security degree equips students with hands-on experience in cyber defense, encryption, penetration testing, and incident response—skills that prepare graduates to thrive in one of today’s fastest-growing career fields.
UAT’s Network Security degree focuses on proactive cyber defense strategies that blend theory with hands-on practice. Students gain experience in encryption, penetration testing, vulnerability assessment, and incident response while building a foundation around the core principles of confidentiality, integrity, and availability.
Graduates of the program will be able to:
Design secure network infrastructures with defense-in-depth strategies.
Install and configure security tools like firewalls, intrusion detection systems, and anti-malware software.
Automate security processes using scripts and system administration tools.
Develop and implement response and recovery plans for incidents, disasters, and business continuity.
Apply legal and ethical best practices in cybersecurity and information governance.
Research, evaluate, and mitigate emerging cyber threats across evolving digital landscapes.
This combination of technical training and practical application ensures UAT graduates are prepared to defend against today’s cyber threats while anticipating the challenges of tomorrow.
UAT stands out as a National Center of Academic Excellence in Cyber Defense (CAE-CD), a designation from the NSA that highlights the program’s quality and rigor. Students benefit from UAT’s Synchronic Learning model, which blends mentorship, hands-on labs, and project-based education. Along the way, they tackle real-world challenges through cyber competitions and proof-of-concept innovations that prepare them for the workforce.
Here are some of the key courses that bring the program to life:
NTW220: Linux I for Technologists – gaining command-line and open-source system experience.
NTW245: Mobile Security and Exploitation– securing modern mobile and cloud environments.
NTW280: Virtualization System Technologies and Administration – exploring virtualization for secure, scalable networks.
NTS305: Information Governance – managing security policies, compliance, and risk.
NTS350: Network Security Monitoring – detecting and responding to threats in real time.
NTS442: Collegiate Cyber Defense Competition – applying skills in competitive, real-world simulations.
UAT’s Network Security graduates are prepared for in-demand careers such as network security engineer, penetration tester, cybersecurity analyst, incident response specialist, and IT security auditor . These roles are critical in industries ranging from healthcare and finance to government, defense, and cloud technology.
Cybersecurity is one of the fastest-growing fields worldwide, with job demand far outpacing supply. A Network Security degree from UAT not only provides the technical expertise employers are looking for, but also ensures students graduate with hands-on experience, industry certifications, and proof-of-concept projects that showcase their ability to solve real-world problems. This makes UAT graduates uniquely equipped to protect data, strengthen systems, and shape the future of cyber defense.
Q1: Do I need to know a lot about computers before starting this program?
No prior expertise is required. UAT starts with the fundamentals and builds up, so whether you’re brand new or already tech-savvy, you’ll find the right level of challenge.
Q2: What kind of person succeeds in network security?
If you’re curious, enjoy solving puzzles, or like the idea of protecting others, you’ll fit right in. Persistence and attention to detail are often more important than prior technical skills.
Q3: Will I get real-world experience while studying?
Yes. UAT emphasizes hands-on learning, with labs, simulations, and even competitions where students defend systems against live cyberattacks. These experiences prepare you for the workforce.
Q4: How expensive is it to study network security at UAT?
UAT offers financial aid for qualifying students, including scholarships and grants. Advisors can walk you through your options to make sure your education is as affordable as possible.
Q5: What’s campus life like for someone studying cybersecurity?
You’ll join a creative, tech-focused community where students collaborate on projects, compete in cyber defense challenges, and share a passion for technology and problem-solving.
Q6: Can I study online if I can’t always be on campus?
Yes. With UAT’s flexible learning model, you can choose on-campus, online, or a mix of both, making it easier to balance your studies with other commitments.
UAT’s Network Security degree blends theory, hands-on labs, and cyber competitions to equip you with the skills to defend networks, protect data, and stay ahead of digital threats.
📍 Tempe, AZ — Real skills. Real impact.
💻 Start defending the digital world at UAT

At University of Advancing Technology (UAT) in Tempe, Arizona, leadership is defined by involvement, innovation, and community impact. During the Fall 2025 semester, Dylan Maxwell who has earned two bachelor's degrees in Advancing Computer Science and Data Science, was honored with the Brook Cayce Legacy Leadership Award, recognizing students who exemplify leadership, service, and dedication throughout their time at UAT.
For Dylan Maxwell, receiving the Brook Cayce Legacy Leadership Award for the Fall 2025 semester was both humbling and meaningful. Beyond the recognition itself, the legacy behind the award made it especially impactful.
“Receiving this award means a lot to me,” Dylan shared. “It made me realize how much I’ve enjoyed my time at UAT and how many great people I’ve gotten to know during my time here.”
The award reflects Dylan’s commitment to leadership, collaboration, and making a positive impact within the UAT community.
Dylan stayed actively involved at UAT through on-campus jobs, an internship, and student organizations, which helped him remain connected to campus life throughout his degree program.
Working on campus provided a daily opportunity to engage with peers, faculty, and staff, while involvement in multiple clubs helped Dylan build meaningful relationships. UAT’s smaller campus environment made it easy to feel connected and involved.
“Once you start meeting people at UAT, it becomes much easier to meet more and really feel like part of the community.”

Many UAT faculty and staff members played an important role in Dylan’s success during his time in Tempe, AZ:
Professor Heather Peters, a math professor, inspired Dylan with her cheerful teaching style, clear explanations, and daily national day traditions.
Professor Dapzury Valenzuela, who taught SIP and Boards, provided invaluable guidance through the Student Innovation Project (SIP) process.
Bree Erickson and Ashley Fuentes, Dylan’s on-campus job managers, offered mentorship and consistent support.
Jake Henningsen assisted with resumes, internships, and career preparation.
From the Portal team, Leslie Hall, Tristan Vaughn, Darla Martinez, and Renee Grauberger helped navigate scheduling and financial planning.
Katy Toerner and Stace Dixon from UAT’s marketing department were especially influential during Dylan’s summer internship, offering hands-on experience in tech-focused marketing.
“I’d absolutely recommend the content creator internship to any student interested in marketing at UAT,” Dylan said.
Among many highlights at UAT, Dylan recalls hosting a cornhole competition with the Workshop Club and working on the first production studio project, Fair Game.
The most memorable moment, however, was presenting his Student Innovation Project, CoPay, on stage.
“Standing on stage and presenting my SIP project was such a proud moment for me.”

As Dylan graduates from University of Advancing Technology in Tempe, Arizona, the future holds exciting opportunities. While awaiting responses from job interviews, Dylan is eager to begin his professional career and apply the skills gained over three years at UAT.
In addition, Dylan plans to pursue freelance work, utilizing skills in programming, graphic design, marketing, and data analytics—a reflection of UAT’s interdisciplinary, hands-on approach to tech education.
Recognized with the Brook Cayce Legacy Leadership Award for the Fall 2025 semester, Dylan Maxwell leaves UAT with a strong foundation in leadership, innovation, and community—ready to make an impact wherever the future leads.
Inspired by Dylan’s journey?
Turn your passion for technology into real-world impact at University of Advancing Technology in Tempe, AZ. Get hands-on experience, build career-ready projects like SIP, and become a leader in tech.
👉 Start your tech degree at UAT today.

CES 2026 highlights artificial intelligence becoming embedded infrastructure, the convergence of hardware and software, and the expanding role of simulation and immersive technology. These trends matter less for the products they showcase and more for the foundational skills they reinforce—systems thinking, security awareness, and applied problem-solving—which shape long-term technology careers.
Image credit: Consumer Technology Association (CTA)® — CES 2026
This blog analyzes the most important technology signals from CES 2026 and explains how they translate into real-world technical skills, career pathways, and education and career decisions. It is written for students, parents, and career-changers trying to separate short-term tech hype from long-term career fundamentals.
This perspective is especially relevant for prospective students, parents evaluating degree ROI, and professionals considering a pivot into technology roles.
Every January, Las Vegas briefly becomes the operating system for the future. Screens glow brighter, demos get louder, and the Consumer Electronics Show (CES) offers a global snapshot of where technology is heading next.
CES is useful for spotting signals.
The real value comes from understanding which of those signals translate into long-term, career-relevant skills.
Because while products change quickly, the underlying technologies—and the knowledge required to build them—evolve more slowly.
CES is not a curriculum. It is not a hiring roadmap.
CES is a showcase of what is technically possible, not what employers are consistently hiring for. Product launches change quickly; foundational skills do not. Education decisions based on CES trends alone often over-index on tools instead of transferable capabilities.
CES runs January 6–9 and showcases emerging consumer and enterprise technologies across artificial intelligence, robotics, hardware, software, immersive media, and connected systems. For students exploring technology careers, CES is best understood not as a list of gadgets, but as a directional indicator of how industries are converging.
The key question isn’t what launched.
It’s what capabilities are becoming foundational.
At CES 2026, artificial intelligence no longer appears as a standalone feature. It shows up as embedded infrastructure across software platforms, hardware systems, and operational environments.
AI is becoming assumed—not optional.
AI as infrastructure reshapes how work is done across multiple disciplines rather than replacing them outright.
Careers most affected include:
Software Engineering
Cybersecurity
Data Engineering and Analytics
Simulation and Game Development
Network and Systems Engineering
In these roles, AI is not a specialization. It is an assumed layer of the technical environment.
Explore AI-focused degree pathways:
https://www.uat.edu/artificial-intelligence-degree
Related disciplines where AI plays a critical role:
https://www.uat.edu/cybersecurity-degree
https://www.uat.edu/software-engineering-degree
Robotics, IoT, autonomous systems, and smart devices now operate as unified systems rather than separate disciplines. Code, hardware, sensors, networks, and physical constraints are designed together.
This convergence means professionals must understand how systems behave holistically—not just how individual components function.
The most resilient tech careers are built on skills that transfer across tools, platforms, and hype cycles.
Skills with the longest shelf life include:
Systems thinking
Secure architecture principles
Applied problem-solving
Debugging complex environments
Cross-disciplinary collaboration
Tools change.
Mental models endure.
Explore robotics and systems-focused programs:
https://www.uat.edu/robotics-engineering-degree
Supporting specialization:
https://www.uat.edu/embedded-systems-degree
Simulation, extended reality, and immersive environments continue to grow across defense, healthcare, cybersecurity training, engineering, and decision-support systems.
These technologies are increasingly used to model complexity, test scenarios, and prepare professionals for high-stakes environments where real-world failure is costly.
Explore immersive and simulation-driven programs:
https://www.uat.edu/game-programming-degree
https://www.uat.edu/virtual-reality-degree
The table below summarizes how CES 2026 signals translate into durable career capabilities.
| CES Signal | Career-Relevant Capability |
|---|---|
| AI everywhere | Systems thinking and data literacy |
| Product demos | Scalable architecture and design |
| Consumer-facing tech | Enterprise and infrastructure systems |
| Rapid platform changes | Technical fundamentals that endure |
Technology evolves quickly.
Foundational skills compound.
CES 2026 reinforces a broader industry reality: successful technology careers are built on understanding systems, not just tools.
The goal is not to predict the next CES headline, but to build skills that remain valuable across multiple technology cycles.
Degree programs aligned with these signals emphasize:
Applied problem-solving
Cross-disciplinary technical knowledge
Security and systems awareness
Adaptability as technology evolves
This alignment prepares students for both current and emerging technology environments.
CES 2026 highlighted AI becoming embedded infrastructure, the convergence of hardware and software, and the continued expansion of simulation and immersive technologies across multiple industries.
CES provides early visibility into where technology is heading. Career-relevant insight comes from identifying which technologies require long-term skills such as systems thinking, security, and applied engineering.
Skills tied to AI systems, cybersecurity, robotics, embedded systems, and simulation are increasingly important as technologies converge and become more complex.
Students should look beyond products and focus on degrees that teach transferable fundamentals—programming, systems design, security, and applied problem-solving—that align with long-term industry needs.
CES influences awareness, not curriculum design. Strong academic programs evolve based on industry adoption, foundational skill requirements, and long-term workforce needs—not product release cycles.
The trends highlighted at CES 2026 reinforce the importance of applied, hands-on education rather than abstract or tool-specific training.
Examples include:
AI infrastructure → software engineering, data science, and cybersecurity foundations
Simulation and immersive systems → game development and real-time simulation programs
Security-by-default design → network engineering and cyber defense curricula
This alignment emphasizes preparing students for long-term relevance rather than short-term trend chasing.
CES 2026 highlights AI as embedded infrastructure, the convergence of hardware and software, and the expanding role of simulation and immersive technology. Together, these trends point to growing demand for foundational skills such as systems thinking, security awareness, and applied technical problem-solving—areas emphasized in advancing technology degree programs at University of Advancing Technology (UAT).
Explore UAT degree programs aligned with emerging technology careers:
https://www.uat.edu/degrees

Fall 2025 Student Innovation Projects (SIPs) at University of Advancing Technology (UAT) in Tempe, Arizona showcased how students turn emerging technology concepts into real, working solutions. From Artificial Intelligence (AI) and Cybersecurity to Game Design and Robotics, each project reflects UAT’s hands-on, industry-driven approach to technology education.
Student Innovation Projects are a core part of UAT’s project-based curriculum, giving students real experience building, testing, and presenting technology solutions before graduation. These projects help students develop portfolios, collaborate across disciplines, and prepare for careers in today’s tech-driven industries.
Below is a recap of the featured Fall 2025 SIPs, highlighting the innovation, skills, and impact behind each student-built project.

Somnia, Baylee Balsimo Ketelhut BEST IN SHOW AWARD WINNER
Somnia is an adventure game concept where you play as a travelling live-streamer exploring a new planet in search of unique content to entertain your simulated virtual audience.
Last Heart Tourney Brandon "Blu" LaVoy
Last Heart Tourney is a competitive board game system meant to create semi-cooperative gameplay. This is done by designing games that can have multiple winners/losers, and give ways to boost one another.
Project Outlook Chrstopher Echaniz
A game mechanic that gives the player the ability to take away aspects of their environment to help them solve puzzles and avoid enemies.
Spectrum Battle System Daniel Parker WORLD CHANGER AWARD WINNER
A game simulator that aims to translate the Autism condition in a way that is both informative and interactive.

Narrative-Conscious Persistence Through Reframing Save/Load as a Mechanically
Embedded, Systemically Causal, and Progression-Critical Player Action in Decision-
Responsive Game Worlds Jenson Searle INGENUITY PRIZE AWARD WINNER
A new way of designing games, allowing players to save the game and not override a prior save but the game develops through the saves and adapts for future game play.
FIGHT CORE DESTROY Nathaniel Andert
FIGHT CORE DESTROY is a prototype 2D robot fighting game with limb damage mechanics.
VR Sword Caleb Carroll
A system that enhances immersion in a VR melee combat by making weapons virtually age and degrade in real time.
The Genesis Record YenLinh Nguyen
A simple and straightforward game utilizing the two main gimmicks of general gameplay use and player response. Players apply these two gimmicks in this minimalistic game to solve puzzles, engage world interaction and combat.

Fruit Scorer Addon Module for Commercial Sectionizer Sean Johnson MOST MARKET VIABLE AWARD WINNER
A simple add-on module to commercial fruit sectionizers allowing the customer to score the fruit wedges simultaneously with a chef's knife.
Find Beauty in Everything... Alexa Tuchtenhagen
Find Beauty in Everything... is a gentle robotic butterfly designed to bring comfort, ease anxiety, and create moments of peace for hospice patients and the families who love them.
S.W.A.V. (Self-Operating Waste Amoving Vehicle) Zachary Lewis
S.W.A.V. is an automated base for a trash bin that can take out the trash for you!
Coil Gun Project Eloy Fernandez
A magnetic coil based projectile propulsion device.
Field Test 420 Matthew Winter
A handheld 24VDC 4-20 mA Signal Generator.
Replica Rings Chelsea Krepps
A new innovative spin on the silicon ring industry. This project creates custom silicon rings that replicate the beauty of metal rings, rather than the simple, bulk produced silicon rings that are already on the market.
Expandable Riot Shield Terrine Martin
A compact, telescoping, defensive system designed for fast, reliable deployment.
One Minute Hire SJ Campbell
One Minute Hire is a service that produces 60-second video resumes for entry-level jobseekers with little-to-no experience.
Cyber Culture on Canvas Emily Lovo
Cyber Culture on Canvas is an art-driven cybersecurity project that turns complex security concepts into original hand-painted canvases to educate, engage, and inspire audiences.
Voice-Coded Planner Lucia Reed
A voice-coded planning system that dynamically restructures task priorities based on user readiness, cognitive load, and moment specific capability rather than fixed chronological scheduling.
ProSave Zoe McGowan
An incremental autosave plugin for adobe premiere pro.
V.E.H. (Video.Editing.Helper.) Gregory Strickland
V.E.H. is an application site that helps edit videos more effectively by scanning through your video, finding mistakes in it and highlighting them on a timeline for you to see, showing the severity, description of the issue, what the issue is and where it happened.
WWMogi Landon Yates
WWMogi is a webscraper that takes an API call requesting leaderboard information from a website, cleans the data and formats it to be displayed via an application.

GitGrub Jerome Reaux Jr. BEST SIP PITCH & VIEWERS CHOICE AWARD WINNER
An app that focuses on bringing late-night cafe back online!
NutriDetect Alexander Garcia Garnica
Scan any food label and get instant allergen warnings.
OpenExonaut Sean Burchett
A game server for a particular game The Decade Deceased Project Exonaut. But also can be torn down and repurposed for similar games.
Interpaws Amari Bullard
Interpaws connects pet owners with the perfect veterinarian through simple, AI-powered conversations.
AstroTune Preston Chapman
AstroTune is a mobile app for android that allows users to control the music players Foobar2000 and DeaDBeeF running on a computer using their phone.
Mystic Card Forge Jackelin Britton
A Web Application that lets players and creators design their own Magic the Gathering cards with authentic detail and style all in a simple, easy to use interface.
Copy Clipboard Nathan Dalu
A smart translation assistant that lives in your system tray. Instead of a multi-step translation process, you can copy text, click the icon and get instant translation without ever leaving the application.
ArtViseAI Sanyerlis Camacaro
An AI Art Application that runs locally on your computer with or without internet access.
Argus Net Protector Daniel Drljaca
Argus Net Protector gives everyday people an easy way to assess and improve their own home network.
CLIND Keegan Heaton
CLIND is an interactive social-media tracking and mindfulness app that helps users reset their minds after every scroll session.
Tailored Learning Melanie Owens
Tailored Learning is an email security plugin that helps spot phishing, impersonation, and malware by analyzing message headers, URLs, and text locally to a SQL database with an audit trail.
Inspired by these Student Innovation Projects? Start your tech degree at UAT in Tempe, AZ, where hands-on learning turns ideas into real-world solutions.

On the Twelfth Day of Techmas, we’re closing out the series with 12 insider tips from University of Advancing Technology's (UAT) leadership and staff to help you thrive. From campus life to classroom success, these quick, practical insights are the perfect way to finish Techmas strong and make the most of your UAT journey.
Valerie Cimarossa Chancellor "Take advantage of the resources you have. Faculty, Student Services, tutors - they’re here for your success. Come with questions, and don’t be afraid to ask for help. There will always be a helping hand available to you, you just have to reach for it."
Jake Henningsen Career Services Coordinator "Don't make projects that pass classes; make projects that pass interviews"
Tristan Vaughn Sr. Student and Career Services Advisor "Trust the process! By beginning larger projects early on, students ensure they can learn the materials and skills necessary to succeed without getting overwhelmed or falling behind."
Brandi Beals Vice President of Student Affairs "Remember; You're Here to Innovate - Don't be afraid to experiment, try bold ideas, prototype often, and fail forward. UAT is a place where technology, creativity, and curiosity collide - embrace it. Treat every class project like a real client assignment. UAT values creation and innovation. The more professionally you approach your coursework, the more impressive your final portfolio becomes. Connect with Faculty early and often. Your professors are industry pros. Ask questions, request feedback, and get to know them, they are one of your strongest success resources."
Lauryn Ford Financial Aid Advisor "Communication is key! We are available to help, and we want to help, but we need your help to do so. Call often, respond quickly and keep us up to date so we can support you!"
Robert Walker Director of Community Affairs "At UAT, the class sizes are small, professors are mentors and the culture is built on seeking understanding. My tip is to advocate for your understanding of the course materials. If you have questions, missed a step or just need additional support, UAT is the place. Ask that clarifying question, gain the clarity you need, everyone here wants to see you succeed."

Cheyenne Peery Student Services Coordinator "There is no shame in asking for help! Utilize the resources we have available- tutors, program support specialists, advisors, professors. It is a strength to ask for help when you need it, not a weakness."
Teagan Findler Program Support Specialist "Please reach out to your professors if you have a questions or need help with course material, assignments, etc. Communication is key!"
Ashely Fuentes Assistant Director of Student Services "How to be successful at UAT: TRY! The biggest pitfall we see students fall into is to stop submitting work, or wait to submit and assignment until it is 'perfect.' There's just no such thing - and what a student might think is only 'okay' work, may be great to the instructor, in terms of meeting the requirements of the assignments. The best way to know is to submit. Always try to meet the requirements and don't be to hard on yourself. Remember: you are expected to learn and grow, not know everything or be 100% perfect all the time!"
Tyler Widener Program Support Specialist "You're going to get out of school what you put into it. So give your best! Come to class in person to ask questions and network. Be a part of student clubs and the community, because no one can go through the journey alone. Give your education your best effort and it'll echo back for the rest of your life."
Emily Hardesty Sr. New Student Advisor "Manage your time wisely and stay organized! Plan your days out using time blocks or a daily schedule. Make sure you are setting aside time to dedicate to your studies. Use a planner or a calendar to track your assignments and deadlines. This will prevent missed assignments and help reduce stress. Make sure to reach out if you need help."
Stace Dixon Director of Digital Marketing "Just show up. It sounds simple, but it’s one of the most powerful habits you can build for long-term success. Showing up, especially when you’re unsure, inexperienced, or facing something new is an act of courage and commitment. When you try anyway and seek feedback, you invite growth. Asking questions isn’t a sign of weakness; it’s an opening for connection. Leaders and peers often want to support your progress, and collaboration naturally strengthens relationships while leading to better outcomes. People genuinely enjoy sharing their experiences and being part of your story. I see this firsthand with the interns I lead. The ones who thrive aren’t always the most skilled on day one. They’re the ones who consistently show up with curiosity, positivity, and the willingness to figure things out as they go. They understand that achievement is a team effort and that stepping into the unknown is how you build confidence. Success rarely requires perfection, but it always requires presence. Get over the hump of fear, take the first step, and trust that you’ll learn what you need once you arrive. Just show up."

BONUS TIP:
Phillip Ferrell National Admissions Rep "Get Involved! UAT has many different clubs, organizations, career events & services that students can utilize on a daily basis to help themselves grow both personally and professionally."
Inspired by today’s Techmas feature? UAT gives students the tools to create what’s next. Inquire or Apply today!

There’s nothing better than kicking back during the holidays—marshmallows roasting, lights twinkling, the whole world slowing down just a little—and sinking into a great podcast. Whether you’re unwinding after a long year or fueling that tech-curious brain of yours, here are 11 tech podcasts we absolutely recommend for your holiday listening lineup:
UAT Tech Tangents – Smart, fresh, and straight from the innovators here at UAT.
StarTalk with Neil deGrasse Tyson – Space, science, and humor collide.
The Changeling – Curious minds meet curious stories.
Vergecast – Everything tech, culture, and gadgets.
On with Kara Swisher – Sharp interviews with sharp people
Possible – Exploring the future through imagination and design.
AZ Tech Podcast – Arizona’s brightest voices in tech innovation.
The CodeNewbie Podcast – For beginners, builders, and lifelong learners.
Reply All (Alex Goldman & Emmanuel Dzotsi) – Internet mysteries you can’t stop listening to.
Darknet Diaries – True stories from the digital underground.
Tech Talker – Tech explained cleanly, quickly, and clearly.
Happy listening—and happy holidays. Enjoy the glow, the cocoa, and the ideas that keep us inspired.

For the tenth day of Techmas we have gathered ten tech tips from University of Advancing Technology's (UAT) Faculty.
Professor Rae Crusoe Advancing Computer Science "I always tell my students to not trust technology, it will let you down. Keep multiple copies of your files!"
Professor Rawad Habib Software Engineering "Technology changes fast, but problem-solving curiosity never go out of style. Don't just learn tools, learn how to learn."
Professor Jake Perrine Human Computer Interaction "Biotechnology and Wearable Technology empowers you to understand your health as an individual, take advantage and get to know yourself on a deeper level."
Curriculum Integrity & Senior Professor Dapzury Valenzuela SIP & Digital Arts "Adopt an agile mentality when tackling large-scale projects. It's easier to make progress iteratively, when setting smaller milestones. Embrace redirection as opportunities to explore, but dont lose sight of your objective, especially when working within time sensitive deadlines. Remember that time can only be spent, not saved. Inception to implementation takes focus, discipline and belief in yourself that it can be done!"

Professor Ryan Murray Digital Maker & Fabrication "Small, fast iterations keep you from investing too much in a design that is not ready."
Professor Heather Peters Mathematics "Technology is an ever-changing field, so diversifying your skill set is critical. Take those extra certification classes that are offered, seek out training for technologies that are unfamiliar, and eve conciser diving into fields that seem completely different from the career path you are considering to widen your skill set and grow your portfolio."
Professor Gabrielle Vosteen Science "AI can help you study by breaking down difficult topics. For example, you can generate practice questions or summarize information. The key is using it as guidance for learning rather than a tool to relate the process. You can ask AI to quiz you. You may even utilize it to explain concepts in different ways, that can make studying fore effective. The goal is to build your critical thinking skills and problem-solving skills. Treat AI like a study partner that boosts your learning process, not as a shortcut."
Professor Sue Ashton Data Science "Don't jump straight into modeling. Spend most of your time on data cleaning and exploration. Those steps determine 80% of your projects success."
Professor Tony Hinton Artificial Intelligence "Take a moment to reflect on the time you have given this year to texting, videos, games, politics, social media or learning tech skills. Next, reflect on your strengths and weaknesses in each area. Are any patterns materializing? This tech fortune cookie says Life is easy, in 2026 you will improve whatever you invest your time in"

Synchronic & General Studies Regent Craig Belanger General Studies "My Tech Tip for this holiday season is to go old school digital by getting yourself a CD player or Digital Audio Player, and maybe a few CDs to feed them. Yes, I hear myself. Why, you might be asking, would anyone forego the ultra-convenient music streaming subscription services like Spotify and Apple Music in favor of even more devices and a limited music library? After all, having the entire history of recorded music at your fingertips is a dream come true for anyone who lived through the dark ages of being a pre-00s music fan. Plus all you need is your phone for playback. So why go old school? First is the fun factor. Both the FiiO DM13 and the Moondream DiscDrop are elegant devices that make the case that CDs 1) offer superior sound to scratchy vinyl records and 2) fit seamlessly into your playback ecosystem. I love my records as much as the next person, but a 40-year-old Clash record has a few miles on it. Meanwhile, down the street, Hiby, Fiio, Astell & Kern, and many others are producing slick Digital Audio Players, or DAPs, that can be used to house tens of thousands of digital files across affordability ranges. In the early iTunes era, we called these mp3 players, but they’ve grown up a lot since then. Imagine your standard form factor for a smartphone except all of the hardware inside is dedicated to audio quality. To add to the convenience, new CD players and DAPs usually have Bluetooth, so you don’t need to change how you or where you listen to music. Next up is the support you can give to your favorite artists by purchasing music files or CDs directly from them on dedicated websites like Bandcamp or the artists’ own websites (or even better, drop some cash at the merch table so they really feel the love). Spotify revenues are notoriously light, with payout of a few dollars per thousand streams so this allows you to offer more direct support in a meaningful way. If you still want to collect vinyl records, those are always available. Plus, when you own the music, playback isn’t subject to signal strength or availability from your streamer. Last is the experience of pure listening enjoyment. If you use a dedicated player, there’s no messages or pop-ups or other unwanted intrusions, there’s just you and your music and everything else can wait.”
BONUS TIPS
Dr. Mark Smith Grad & Business Technology "New technologies are wonderful tools with potential for an endless amount of uses. Train yourself to always look for potential new angles in which you can use these tools. This is where innovation and creation live. The "success" in technology today is not in creating but harnessing in a productive manner for mass adoption. So, dive headfirst into all the trends in technology and brainstorm the potential uses. Many of them will go no where or not be feasible but eventually you will find those world changing ideas."
Dr. Briant Becote Cyber Security "Verify before you click. Treat every unexpected link, attachment, or login prompt as hostile until proven otherwise. Hover to inspect URLs, and when in doubt navigate to the site manually."
Unwrap even more innovation—explore UAT degrees built for future tech creators.

On the ninth day of UAT’s Techmas, we’re celebrating the joy of play with nine fun gadgets that spark creativity, wonder, and a little holiday magic! From flying drones and smart robots to glowing LED masks and meditative art boards, these innovative tools bring laughter, inspiration, and interactive fun to your season. Whether you’re looking for unique gifts or ways to make your holiday downtime more exciting, these gadgets are sure to light up your festivities.

Meet your high-tech holiday helper! This smart, roaming robot captures photos and videos, monitors your space, and even interacts with pets—perfect for keeping an eye on your festive décor while spreading a little extra cheer.

Soar into the season with this compact drone that makes aerial photography and playful adventures effortless. Capture snowy landscapes, holiday lights, or family celebrations from breathtaking new angles.

Bring music to your holiday celebrations without the hassle of strings! This digital guitar teaches, inspires, and lets you jam along to your favorite festive tunes anytime, anywhere.

Light up your holidays! These customizable, colorful wall panels respond to music and motion, turning any room into a dazzling winter wonderland of fun and creativity.

Unleash your holiday imagination! This compact 3D printer lets you design and print unique ornaments, gifts, or decorations, adding a personalized touch to your festive season.

Keep your space merry and clean! This tiny, fun-to-use vacuum tackles crumbs, dust, and clutter, so your desk or crafting area stays sparkling through all your holiday projects.
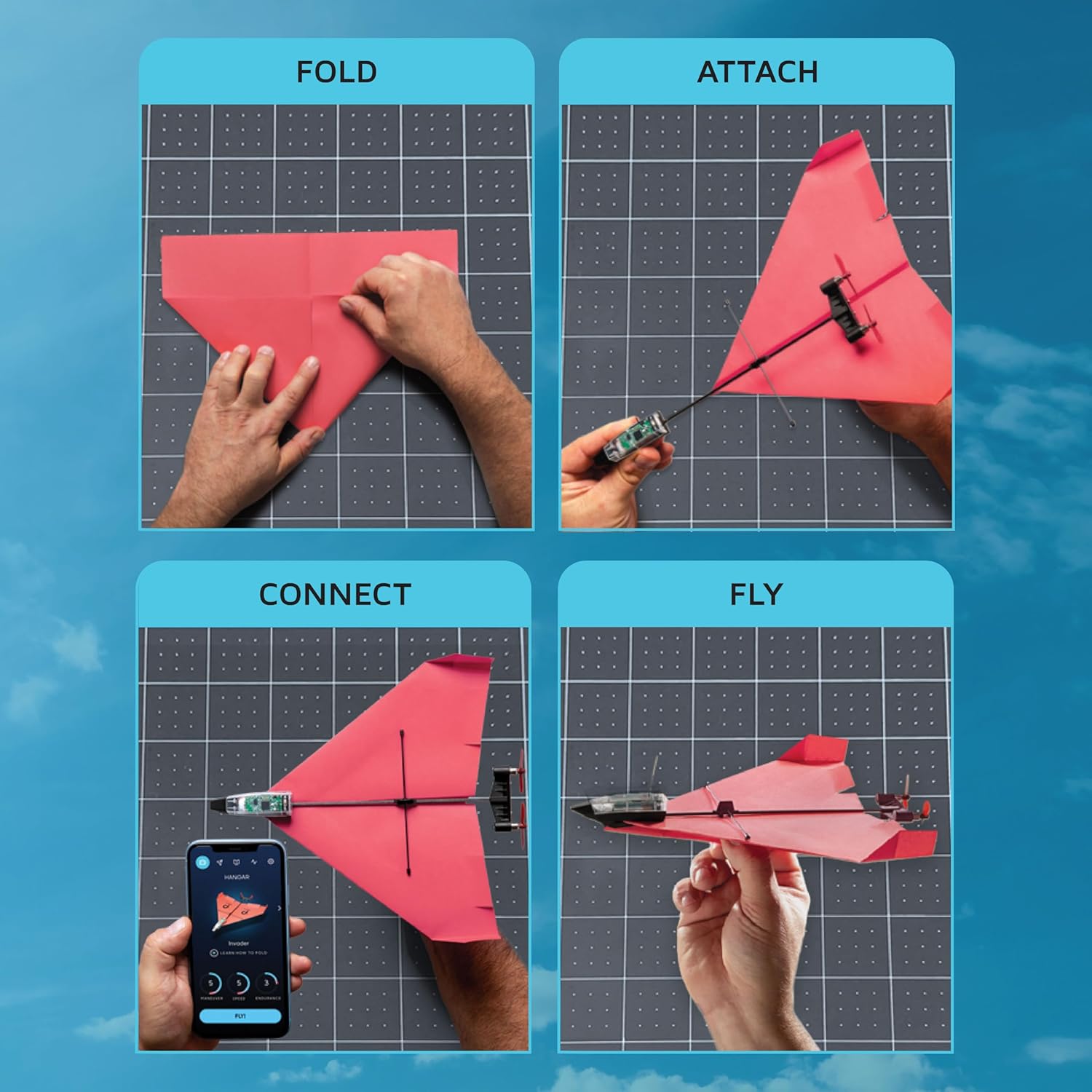
Combine classic holiday fun with modern tech! Fold, fly, and control paper planes with your phone for hours of playful, festive entertainment—perfect for family game nights.

Relax and embrace the holiday spirit with creativity and mindfulness. Paint with water and watch your designs magically fade away, giving you a meditative break from the seasonal hustle and bustle.

Shine bright at holiday parties! This glowing, customizable mask displays animations, messages, or festive designs, making it the perfect statement piece for celebrations, cosplay, or cozy winter fun.
Love exploring new gear? Build the next generation of it at UAT.

December holidays are a month of distilled fun. Without taking away from moments with family and friends, tasty meals, and reflecting on the year nearly done, the holidays and presents go together like eggnog in my coffee (or whatever combo of joy that you happen to like). In preparation, I sat down after devouring my Thanksgiving bird + trimmings and curated my list of favorite tech gadgets for 2025. I am sharing them here in case you have folks asking about something tech-frivolous that you would like this season.
There is something inherently "dark side" about playing darts during winter. Maybe I only sense rogues and villains throwing darts when the temps dip down because during the dark months, days are short and darkness has the upper hand. So in that spirit, sign me up for some high-quality Darth Vader-themed darts.

I do like my coffee. Every day, I kick off with the single best mug that my just-awakened eyes can navigate. Good coffee requires good beans. And when it comes to my friends, arabica and canephora, fresh = good. Hide them from light and air, so when you release, goodness happens. To make my new-day aspirations easier, I have my eye on this rechargeable vacuum canister that puts my beans into restful hibernation until just when I need them.
I have excellent memories of getting up on winter days around 4:00 a.m. to catch the ski bus to the Sunrise slopes of the White Mountains. The bus would deliver me with lift tickets in hand at 8:30 a.m. to spend a day sliding down mountains. During the dark five-hour drive back, a slightly more sore version of me would grab my original Game Boy, conveniently stowed in my ski jacket pocket, along with a stack of cartridges. Dark roads and time would slide by while playing side scrollers like Prince of Persia and puzzle games like Tetris. I have no idea what happened to that old Game Boy, but retro recreations now exist that mash up all the classic handhelds. Fueled by cheap memory and nostalgia, these clones offer thousands of my old games to enjoy while on a holiday break.
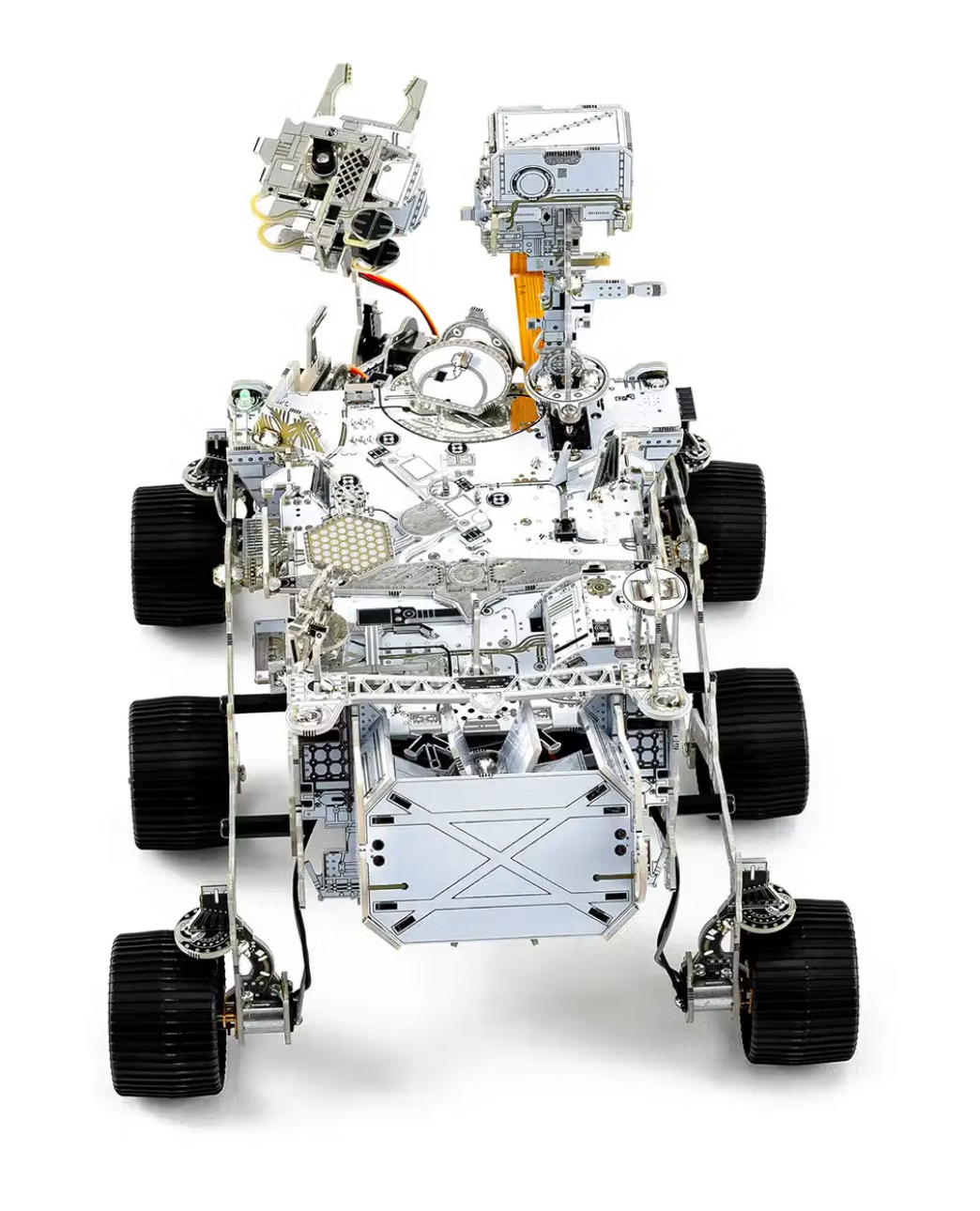
The Perseverance Rover is one of the great marvels of human technological achievement. This six-wheeled embodiment of "never going to stop" left Earth in 2020 and has spent the last 5 years exploring Jezero Crater. A few months ago, Perseverance detected electrical charges in the air that match the profile of lightning. I am never going to get to Mars and shake Perseverance's robotic arm. Still, I could build a homebrew version, AI it up with this kit, and give it a well-deserved high five.

My home includes Kipp, the border collie. This means each and every day, a low-grade sheen of soft tuxedo black and white fur coats my floors. I love my pup. The same is not true for vacuuming up after him. Especially when I rationalize that I personally have no hair and do not require floor clean-up. Any crumbs I leave are nibbled up by Kipp anyway. Problem solved with a decent vac'bot. The AI versions of these map my house, vacuum, mop, and empty themselves into a bin. And if a new puppy shows up and has an accident, these vac'bots have enough AI to avoid the gooey bits.
Sometimes I like gifts that are only vaguely useful, yet the idea is deeply fun. This is where a haptic vest comes in, knocking me around a bit as if I were at that concert or taking a hit. I don't know how many games support it, or even if any thumps from my Beats noise-cancelling headphones would translate into chest vibrations. But spending a day testing it out to see what it does and how close we are getting to Ready Player One would be holiday time nicely spent. And besides, "woojer" is really a fun word to say.

There are many days when I am pinned down for hours listening to what feels like a stew of problems, risks, other people's bad days, and stuff I need to sort out. My go-to solution is some combination of gym, pizza, pup, and family. But those all happen if / when I escape the day. It would be bliss to take it down a few notches while still sitting in those time-dilating meetings. This is the reason why the Truvaga Nerve Stimulator caught my eye. This nifty IoT device can be discreetly held in my hand so that when I feel a fight-or-flight moment coming on, I hold it up to the Vagus nerve in my neck (next to a major blood vessel) and let the Truvaga spend two minutes telling my nervous system to chill out.
So there is my list for 2025. With any luck, some of these will show up under my tree. I hope the same plays out for you!
Dr B.
From holiday tech thrills to hands-on innovation—take the next step with UAT. Apply or inquire today!

On the seventh day of UAT’s Techmas, we’re turning up the holiday cheer with seven wearables designed to make life easier—and a lot more festive! From smart rings that track your wellness to AR glasses that add a touch of magic to your daily routine, these gadgets blend innovation, convenience, and a sprinkle of holiday fun. Whether you’re shopping for yourself or looking for the perfect gift, these tech-savvy tools are sure to keep your season merry, bright, and effortlessly organized.

Stay merry and bright all season long! This smart sensor tracks your hydration in real time and sends gentle reminders to drink water, helping you feel energized and ready to enjoy every holiday gathering and snowy adventure.

Experience a little holiday magic hands-free! These AR glasses overlay digital information onto the real world, making it easy to check your gift lists, follow festive recipes, or stream your favorite seasonal movies while keeping your hands free for decorating and celebrating.

Keep calm amid the holiday hustle and bustle. Muse guides meditation and tracks focus, helping you reduce stress, recharge your mind, and savor quiet, peaceful moments during this busy season.

After days filled with shopping, parties, and celebrations, wind down with these tiny earbuds. They block disruptive sounds and provide soothing audio to help you get deep, restful sleep, so you wake up refreshed and ready for more festive fun.

A sleek, stylish ring that keeps track of your activity, sleep, and overall wellness. Whether you’re dashing through holiday errands or cozying up by the fire, it gives insights to keep you balanced and feeling your best all season.

Start every morning feeling like it’s Christmas Day! This smart mask monitors your sleep patterns and gently wakes you at the perfect moment, ensuring you’re refreshed and ready to make the most of every holiday moment.
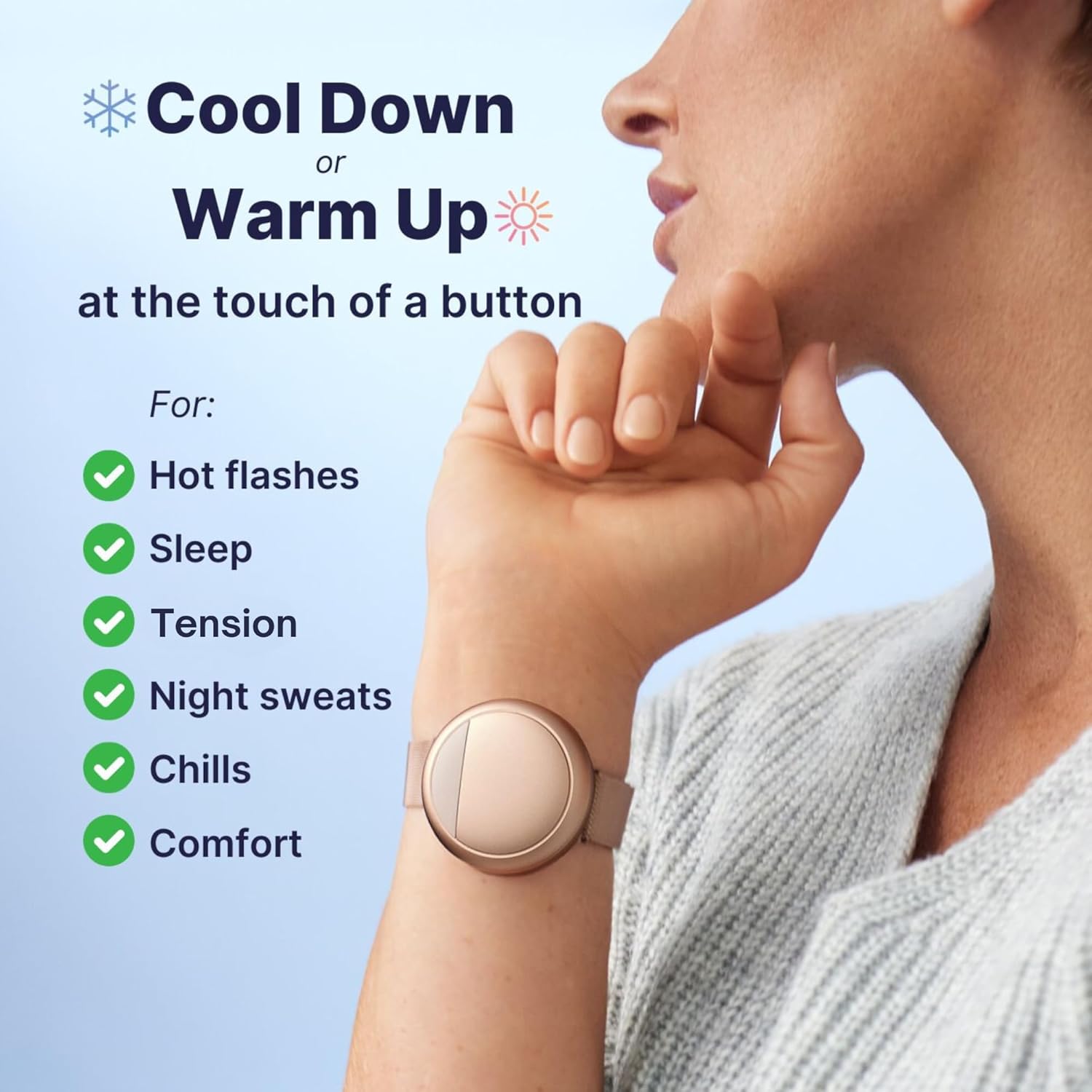
Deck the halls without breaking a sweat! This innovative bracelet lets you instantly adjust your personal temperature, keeping you cozy or cool during chilly winter nights or lively holiday parties.
Like what you saw today? Learn the tech behind these tools at UAT.

On the 6th day of Techmas, we’re celebrating University of Advancing Technology's (UAT) six top blogs of 2025! From Artificial Intelligence (AI) art reaching the Moon to award-winning hackathon wins, immersive experiences at CactusCon, Student Innovation Projects (SIP), esports community highlights, and top Niche rankings, these stories showcase the creativity, skill, and innovation that make UAT students stand out.
1. Hacking, Learning & Networking: CactusCon 2025 By Avery Willets
UAT student Avery Willets describes his experience at CactusCon 2025, where they explored cutting-edge cybersecurity tools, attended talks on red-team tactics and hash-cracking, gained leadership insights, and connected with Arizona’s vibrant cyber community.
2. Spring Innovations Unleashed: Highlighting the Spring 2025 Student Innovation Projects By Katy Toerner
Spring 2025 Student Innovation Projects Spotlight, featuring tools and games that push creative and technical boundaries—from a 3D-to-2D animation converter to an immersive RTS game and a customizable audio plugin—showcasing the innovation driving UAT students’ work.
3. UAT Student's AI Art makes its way from Times Square to Space! By Katy Toerner
UAT student Vanessa Camacaro's AI-generated artwork — previously displayed in Times Square — was launched into space aboard the Firefly Blue Ghost Moon Lander aboard a SpaceX rocket, landing on the Moon at Mare Crisium on March 2, 2025. The piece, “La Vie En Rose,” will become part of a lunar museum — marking an extraordinary blend of AI art, human creativity, and space exploration.
4. Wyverns Gaming & Esports Club By Jayce Jakubowski
UAT’s Wyverns Gaming & Esports Club, one of the campus’s largest student groups, offering a welcoming space for both competitive players and casual gamers. Focused on community, stress relief, and connection, the club gives students a fun, supportive outlet to unwind, build skills, and get involved in campus life through gaming.

5. UAT Ranked among the Best: A top choice for Design, Safety, and Student Life By Katy Toerner
UAT’s strong performance in the 2025 Niche rankings — including being named #1 in Arizona for Computer Science and #1 in Arizona for Design.
It also notes other high ranks: #2 in the state for Information Technology, #2 for dorm quality, #3 for student life and campus safety, and top spots for food, location, and overall campus environment.
6. UAT Students win Hack The Future: Phoenix Hackathon By Robert Walker
UAT students Keegan Heaton and Ozzy James took first place at the SeedAI Hackathon in Phoenix, demonstrating their expertise in AI and cybersecurity. Their winning project highlighted real-world problem-solving skills and UAT’s focus on hands-on, practical learning.
Join the holiday tech celebration—your future in tech starts at UAT. Learn More about all UAT has to offer students today!

On the fifth day of UAT’s annual Techmas, we’re hitting play! 🎮 Today, we’re spotlighting five games that come with the coveted UAT professor seal of approval—titles that aren’t just fun, but also showcase creativity, innovation, and lessons worth learning. Whether you’re a hardcore gamer or just looking for something engaging to try this holiday season, these picks are guaranteed to level up your downtime.
Instructor RaLen Watson-Davis Game Art & Animation "The game that gets my seal of approval is Hi-Fi Rush! This game is a rhythm action game, and it play similar to Devil May Cry. Everything in the game moves to the beat of the music, from the environment down to the combat! Along with some great rock genre songs, the art style has an awesome comic book style look and plays like a dream. I like fighting games and I like music, and the bonus of having a sick art style really made this game stand out to me! It innovates on both action games and rhythm games with the gameplay and mechanics introduced. This game is great for anyone to play, so give it a shot! It's fun and satisfying to play!"
Professor Dane Cavanaugh Toft Game Studies "My favorite game would have to be "Splatoon 3". It is a 3rd person 4v4 shooter created by Nintendo. The player is a character that can transform between two forms, a "Kid" form and a "Squid" form. The goal of the game is to best the opponent team in "Turf Wars" where the goal is not to always get kills on other players like other shooters but instead to paint the most turf on the ground at the end of a 3 minute fast paced match. The players use a variety of weapons to dish out massive paint such as giant paint rollers, buckets to fling ink around the map, or even sniper rifles shaped like a giant pencil. "
Dr. Hue Henry Game Programming "World of Warcraft- Peaking in 2010 at over 12 million subscribers ( that's more than the population of Sweden! ) WoW is the most popular MMORPG of all time. Even now, more than 20 years after the game was released, there are still millions of passionate players who spend their free time hanging out in Azeroth. Understanding how this game can entertain this massive world-wide audience for such an incredibly long time is critical for any game design students who want to make their own popular, long-lasting games. Plus, it's a lot of fun! "
Game Studies Regent Derric Clark Game Design & Virtual Reality "Stardew Valley is an open-ended cozy RPG originally released on February 26, 2016. Stardew Valley’s longevity is fostered by continuous updates over the last 10 years including multiplayer support, new events, new areas, and new gameplay systems. The 1.6 update boosted the average active daily players on Steam with Stardew Valley regularly ranking in the top 50 and often in the top 25. The game even hit over 200,000 concurrent players in 2024. After inheriting your Grandpa’s farm, you move to Stardew Valley and start your adventures. Meeting the local villagers, starting your farm, and exploring the Valley kick off the gameplay and the player experience within the game. Starting with your Grandpa’s old tools, you will Farm, Forage, Fish, Mine, and Fight your way through the story arcs, task completion, and upgrades to many systems in the game over hours and hours of gameplay and potentially, multiple play through. This retro graphics, cozy game has an amazing amount of content and with modding, has unlimited possibilities for gameplay style and fun."
Professor Jake Perrine Esports Coach "I have been playing this one game that came out last month a lot called 'ARC Raiders'. Its a multiplayer extraction shooter where you fight other players and robots for better equipment and weapons. "
Ready to level up your tech journey? Apply or inquire at UAT today.

On the fourth day of Techmas, University of Advancing Technology's (UAT) Cyber Security Faculty are here to help you stay safe online this holiday season! From phishing scams disguised as festive deals to Wi-Fi risks while shopping on the go, the digital world can be just as tricky as it is convenient. That’s why they have rounded up their favorite tips to protect your data, devices, and digital identity—so you can focus on the joy of the season without worrying about cyber Grinches.

Dr. Briant Becote "Use Multi-Factor Authentication (MFA) whenever possible- it helps ensure your accounts are protected, even if your passwords are compromised."

Professor Aaron Rodriguez "Password managers might not be flashy, but your wallet will definitely appreciate the extra protection. Secure your accounts - secure your cash."
.jpg)
Professor Sarah Bunce "Use a password manager to have separate passwords for each of your accounts. Reused or weak passwords is one of the most common ways attackers steal your information."

Professor Adam Zeiner " Avoid Public Wi-Fi for Shopping: Never enter passwords or credit card numbers while on free Wi-Fi at a cafe, airport, or hotel. Hackers on the same network can "sniff" this traffic."
Keep the Techmas spirit going! 🎄 Apply to UAT today and start unwrapping your future in tech.

On the Third Day of Techmas, we’re celebrating the power of staying connected—anytime, anywhere.
Today’s spotlight is all about smart devices that keep your digital world running smoothly, help you stay in sync with what matters, and bring a little extra convenience to the season. From streamlining your routines to enhancing your productivity, these three smart picks keep you plugged in throughout the holidays and beyond.
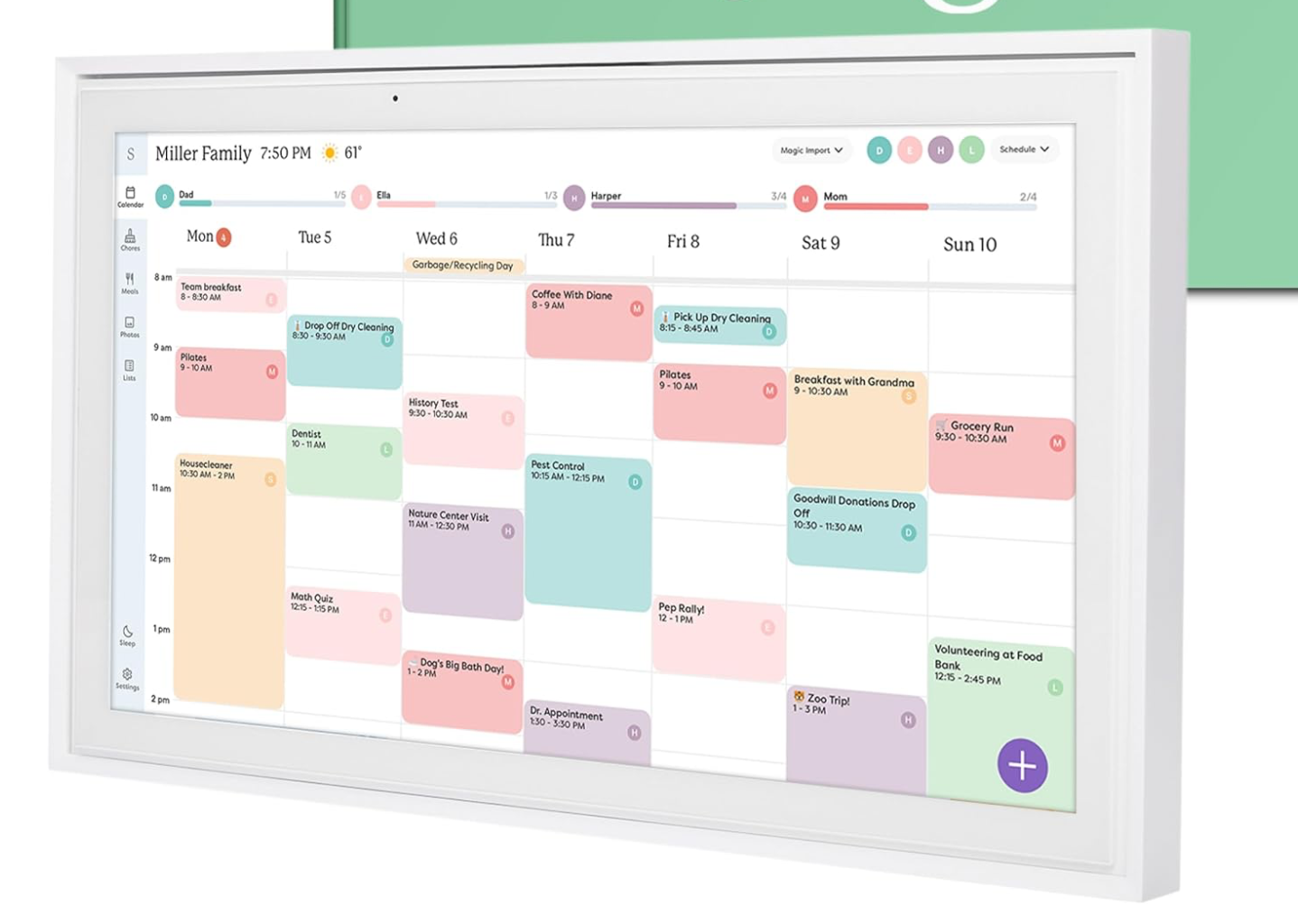
Stay connected and on track in the new year with the Skylight Calendar. Skylight’s Smart Wall Planner is a touchscreen digital calendar designed to keep people organized. It syncs effortlessly with major calendar platforms, mounts on the wall or sits on a countertop, and serves as a central hub for schedules, chores, and meal planning. With interactive task lists, color-coding, and remote access through the Skylight app, it keeps everyone connected from anywhere. Upgrading to the optional Plus Plan adds features like Magic Import, rewards, photo screensavers, and enhanced planning tools.

The Nest Hub Max is a 10‑inch smart display from Google with a touchscreen, built-in speakers, a wide-angle camera, and smart-home controls. It lets you watch videos, stream music, manage smart devices, and make video calls. Features like auto-framing and Face Match enhance video calls, while a physical switch ensures camera and microphone privacy. Its stereo speakers deliver richer sound for music, videos, and more. This device keeps the family connected all year long.

The Plaud Note Pro is a credit‑card‑sized AI-powered notetaker that records calls or in-person conversations, auto-transcribes them, and generates smart summaries. It has a small AMOLED display for recording status and battery, plus a 4-mic array that captures voices clearly up to 16 ft. A long press starts recording, while a short tap highlights key moments for the Artificial Intelligence (AI) to prioritize. Ultra-slim and lightweight, it’s easy to carry and ideal for meetings, classes, or interviews. The Plaud Note Pro is a great gift for the busy student or professional in your life.
From cutting-edge gadgets to the minds who create them—start your tech degree at UAT.

On the Second Day of Techmas, we’re highlighting forward-thinking technologies that push innovation in meaningful ways. Today’s focus is all about going green, as we feature two sustainable tools making a real impact on how we live, work and consume.
This smart home management tool gives users full visibility into their home’s energy consumption—room by room, device by device. Savant Smart Budget helps homeowners track usage patterns, identify high-draw electronics, and set monthly energy goals that encourage mindful consumption. By blending convenience with real-time insights, it empowers users to shrink their energy footprint while saving on utility costs. A greener world and a happier wallet? That’s holiday magic.

Say goodbye to piles of notebooks and printed documents. The reMarkable Paper Pro turns your workflows digital with a natural, pen-to-paper writing experience—minus the waste. It lets users sketch, annotate, brainstorm, and organize work across devices, all without consuming a single sheet of paper. For students, creators, technologists and busy professionals, it’s a sustainability win wrapped in minimalist design.
Whether you're reducing daily waste or managing your home’s energy smarter, these eco-friendly tools prove that innovation and sustainability go hand in hand. Stay tuned for Day 3 of Techmas as we unwrap more future-forward favorites!
Today’s Techmas innovation is just the start—explore AI, robotics, and emerging tech at UAT.

The moment we watched its display rise and stretch upward, we knew this was more than a cool prototype. Lenovo’s rollable OLED screen smoothly transitions from a traditional 14" laptop display into a tall, productivity-boosting 16.7" vertical panel with a tap or gesture. It’s the kind of innovation that instantly changes how you work — offering more room for coding, research, editing, and multitasking without adding bulk to your bag.

Inside, the ThinkBook Plus Gen 6 Rollable packs Intel’s latest Artificial Intelligence (AI)-ready processors, giving students, creators, and tech innovators the performance they need to build, design, and explore without limits. Paired with a premium build, advanced on-device AI features, and a futuristic form factor that still feels practical, this laptop stands out as one of the most exciting releases of the year.
Seeing it at CES made one thing clear: rollable displays aren’t just the future — they’re here. And this device captures exactly what we love most about emerging tech: bold ideas, smart engineering, and tools that make creative problem-solving even more powerful.
As we kick off the 12 Days of Techmas, the Lenovo ThinkBook Plus Gen 6 Rollable sets the tone — innovative, inspiring, and ready to fuel the next generation of tech talent.
Love today’s tech spotlight? Unwrap🎁 even more inspiration with UAT's forward-thinking degrees!